ImaginaryCTF-2024 Writeup
ImaginaryCTF-2024

FORENSICS
bom
Description
楣瑦筴栴瑟楳渷彣桩渳獥
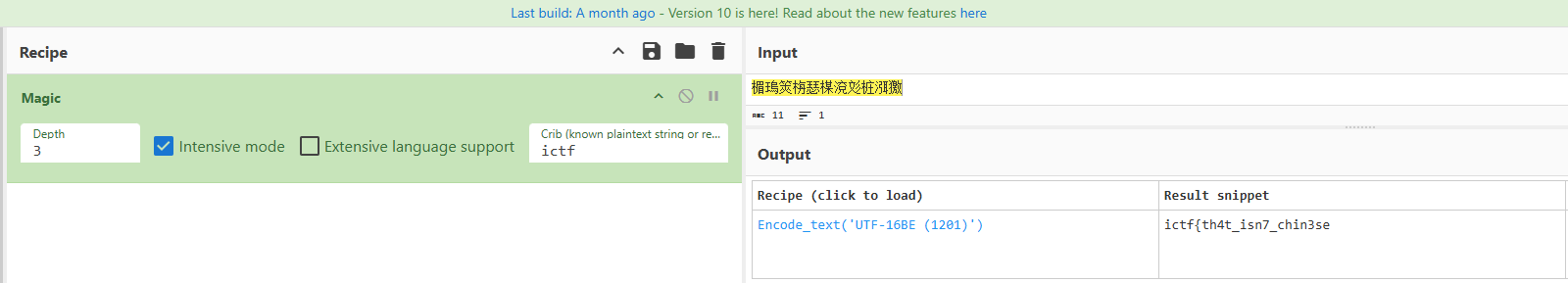
ictf{th4t_isn7_chin3se}
packed
Description
Packet Tracer is a cross-platform visual simulation tool designed by Cisco Systems that allows users to create network topologies and imitate modern computer networks. The software allows users to simulate the configuration of Cisco routers and switches using a simulated command line interface. (
same attachment as routed)
在线工具提取
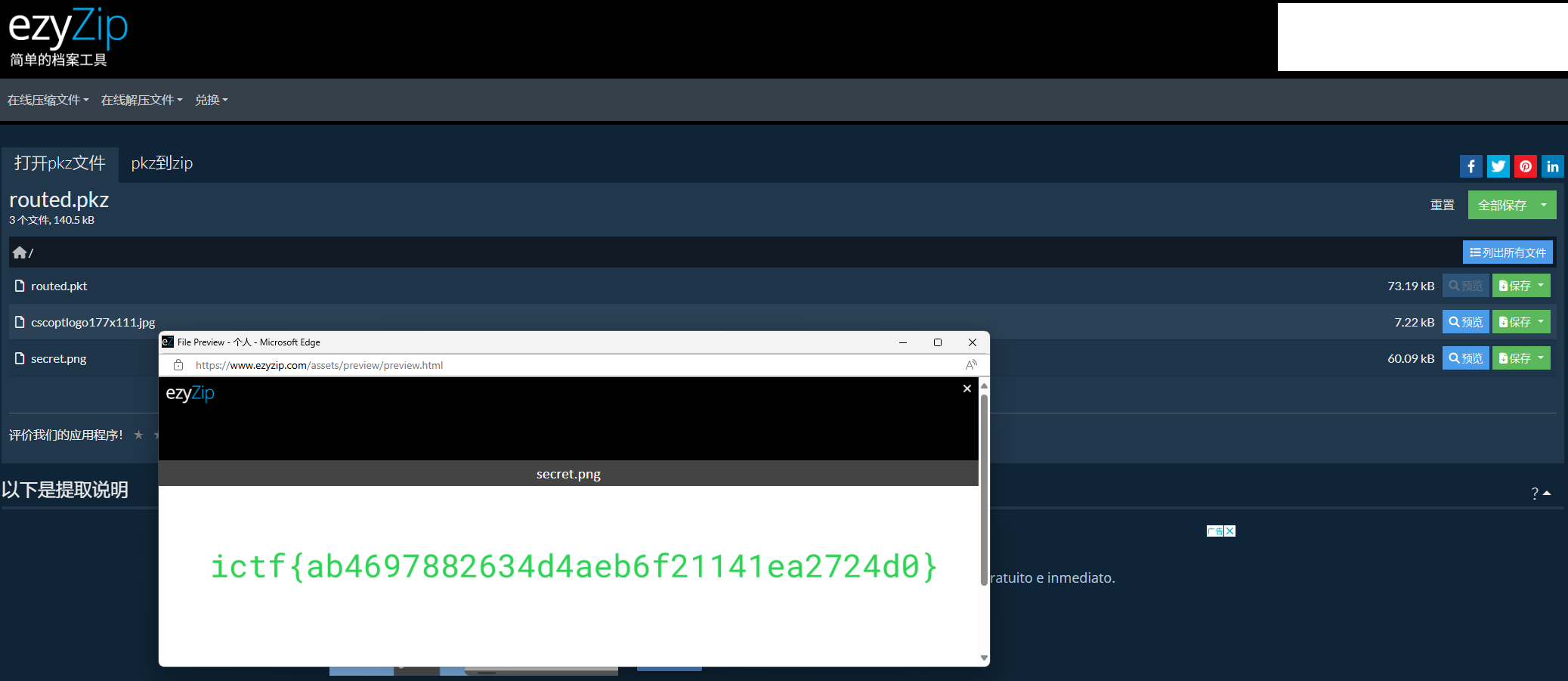
ictf{ab4697882634d4aeb6f21141ea2724d0}
cartesian-1
Description
THIS IS AN OSINT CHALLENGE.
Greetings. You have been tasked with investigating the whereabouts of a potential recruit. To perform this top-secret background check, we must gather as much information as possible.
Please investigate Terrence Descartes. We know that his social accounts are relatively new, so please do not attack anything out of scope. For the sake of this series of challenges, nothing pertaining to Terry has existed before July 17, 2024. Do not investigate anything posted online before then.
查到 github 账户
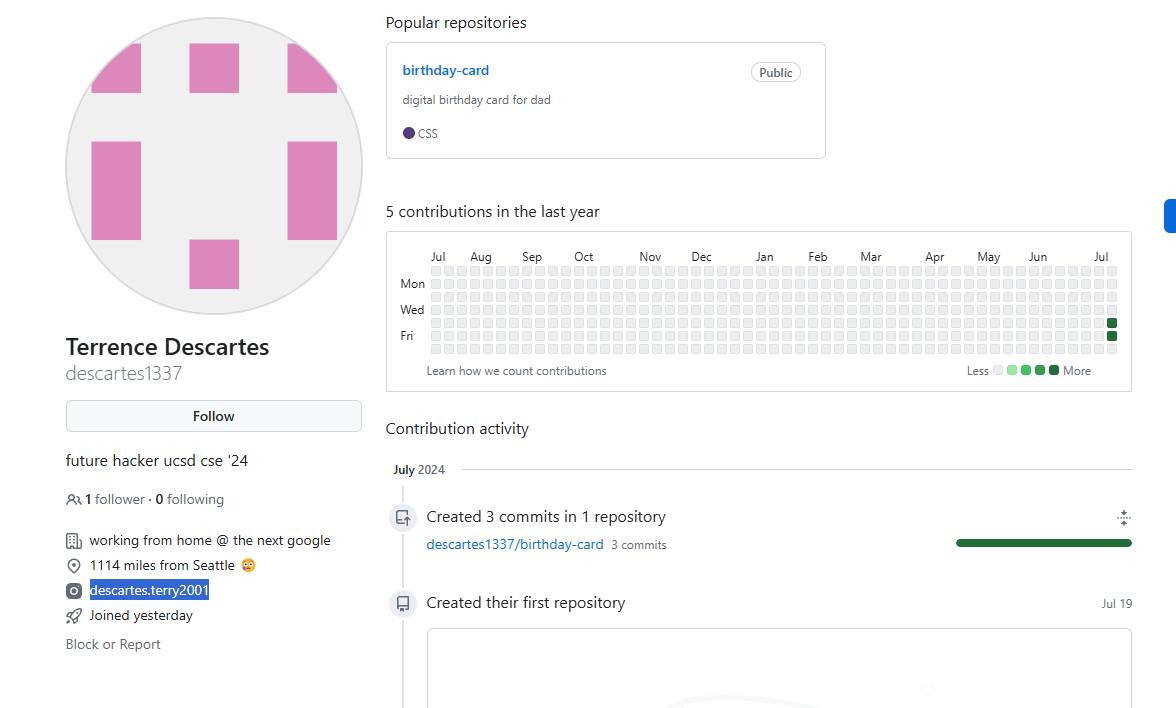
继续搜索 ins 账号
查看最新 动态
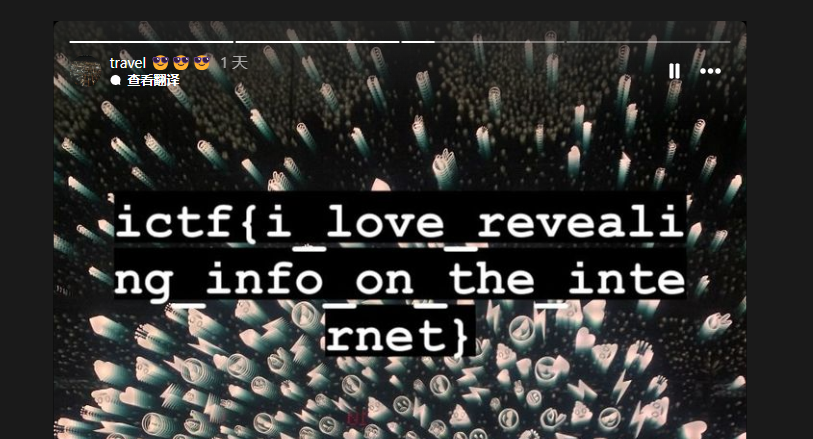
ictf{i_love_revealing_info_on_the_internet}
routed
Description
Can you dig a bit deeper? (same attachment as packed)
There are some fake flags; this is unintentional. The real flag is not in plaintext.
1 | |
Attachments
https://cybersharing.net/s/266989fb9d6c56b1
使用 Cisco Packet Tracer 打开 routed.pkz 查看历史命令 明文的flag 都不对
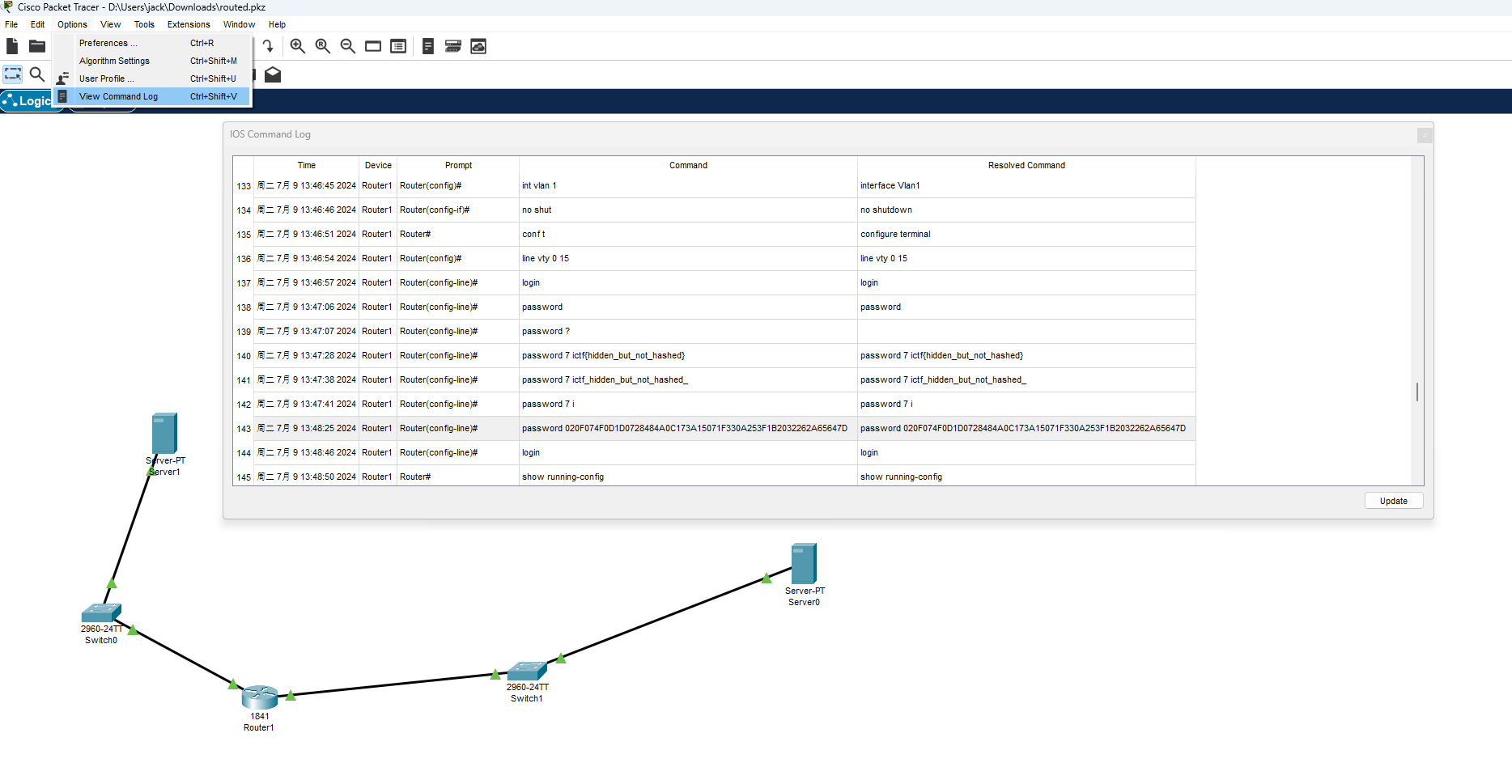
解密 password 7 使用最后一次登录的密码
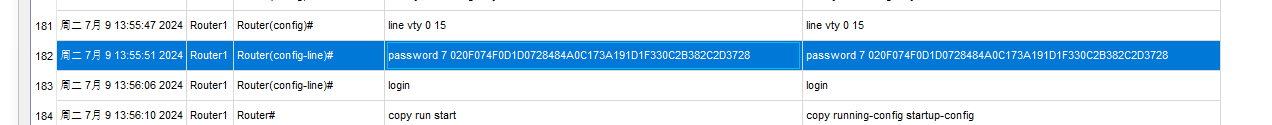
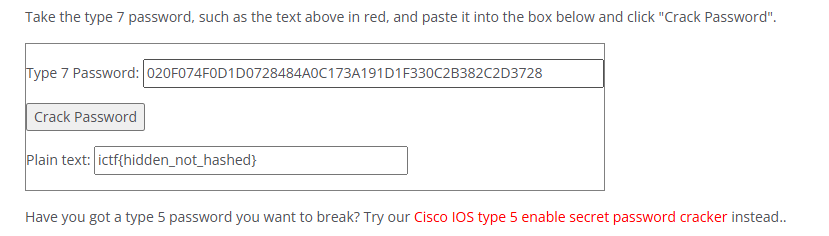
ictf{hidden_not_hashed}
crash
Description
I didn’t save my work…
Attachments
https://storage.googleapis.com/ictf-2024-files/dump.vmem
MemProcFS-Analyzer 打开内存镜像 在 timeline_web.csv 中发现流量了 base64 解密网页
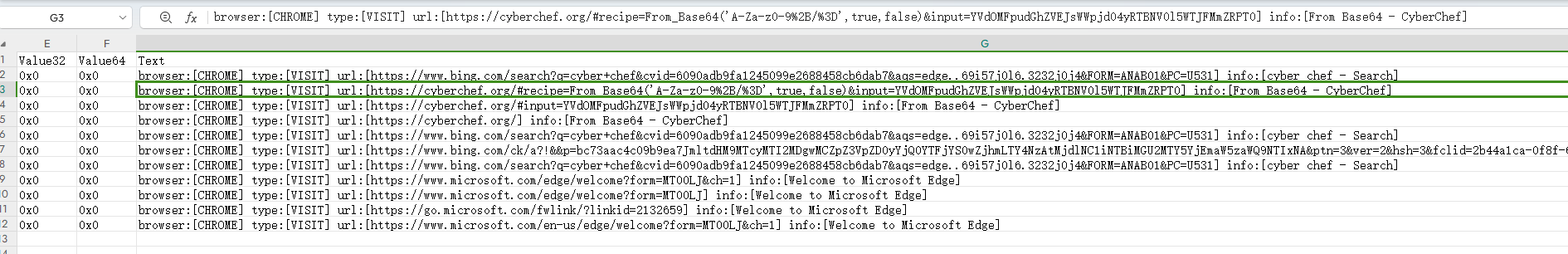
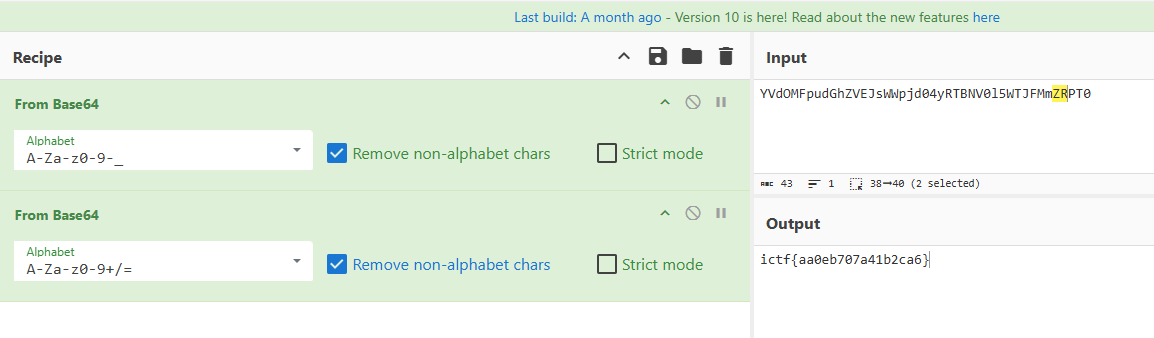 ictf{aa0eb707a41b2ca6}
ictf{aa0eb707a41b2ca6}
REVERSING
unoriginal
Description
i like elf reversing
Attachments
https://cybersharing.net/s/8330af8ef6c673a8
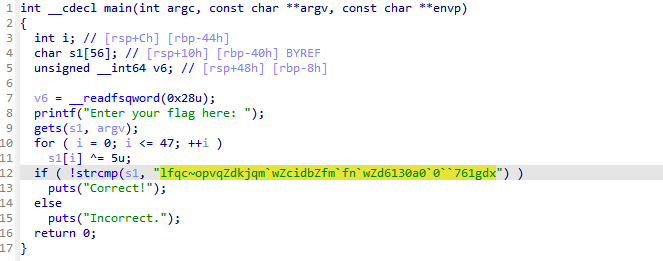
xor 5 得到flag
1 | |
ictf{just_another_flag_checker_a3465d5e5ee234ba}
CRYPTO
base64
Description
yet another base64 decoding challenge
Attachments
https://cybersharing.net/s/8c2a3e4e78a0161f
1 | |
ictf{b4se_c0nv3rs1on_ftw_236680982d9e8449}